
The Lightning Network is an off-chain solution for the Bitcoin blockchain. It is a “second layer solution”. With such technologies, actions for a blockchain can be outsourced and processed in an external system. Such technologies are one of the best known and best solutions for scaling blockchains.
While the Bitcoin blockchain can handle around 7 transactions per second, it is possible with the Lightning Network to handle up to 1,000,000 transactions per second within one channel. In this article we explain what a channel is. The transactions can be transferred almost in real time and cost almost nothing, sometimes even nothing at all.
Therefore, Lightning is also ideal for paying for microtransactions or paying for certain services on a regular basis. The processes are fast, cheap, secure and anonymous. International financial transactions are also possible with Lighting Network. Here, the participants also benefit from the speed and the very low transaction fees. This is possible within seconds, also by exchanging real currencies.

What is the point of the Lightning Network?
Off the blockchain, scalability isn’t an issue, and scaling is quicker off the blockchain than on a giant blockchain like Bitcoin. At the same time, the Bitcoin blockchain can remain as safe as possible. The low speed and the high computing power required ensures that the bitcoins and the transactions associated with them are maximally secure. Special solutions such as the Lightning Network use the security of the Bitcoin blockchain and integrate their own functions, such as higher speed when transferring transactions.
The Bitcoin Lightning Network was officially unveiled in 2015 and has been available on the Bitcoin mainnet since around 2018. The public alpha release took place on January 10, 2017. Since its official launch, the Lightning Network has continued to grow and more and more users are using Lightning to process their transactions quickly. The Bitcoin blockchain reached its limits as early as 2017, as not all transactions could be processed in the necessary time.
The situation was a threat to the entire blockchain, as it could not be used as a global currency under these circumstances. The Lightning Network (LN) is a tool that can be used against such problems. Simply put, LN allows transactions to be sent without requiring and burdening the blockchain. The transactions take place in an intermediate layer, relieve the blockchain and at the same time ensure an enormous transaction speed.
The Lightning Network is a “second layer” payment protocol that works on a blockchain (usually Bitcoin). It enables instant transactions between participating nodes and was developed as a solution to the Bitcoin scalability problem. Two parties can transact quickly and cheaply via Lightning. However, peer-to-peer technology can also be used to integrate more participants who exchange bitcoins with each other.
The Lightning Network can process transactions on Bitcoin’s blockchain without requiring energy-hungry mining. For this to work, the use of off-chain technologies is almost essential. Lightning Network is basically another payment network for Bitcoin. The Lightning Network is also ideal for sending smaller transactions, as the fees are much lower than in the conventional blockchain.
More anonymity in the Lightning Network
Added to this is the comprehensive anonymity of use. Lightning Network is highly secure. At the same time, security in the Bitcoin blockchain remains as high as possible. Anonymity is provided by Lightning. For example, there is no transaction history here. Of course, every user can create such a history himself, but there is no such history in the network itself. If you’re not part of a channel, you can’t track checkouts. The level of anonymity is therefore very high.
Transactions are settled on the Bitcoin blockchain using Satoshis (SAT). A SAT is equal to 100,000,000 of a bitcoin. Due to the increasing value of bitcoins, it may make sense to further split SAT in the future. This can hardly be implemented in the Bitcoin blockchain, since the division would be far too complicated. In the Lightning Network, however, this is possible without any problems, since Lightning is much more flexible.
Development of the flash payment method
If you want to delve deeper into the topic, you can read the Lightning White Paper by Joseph Poon and Thaddeus Dryja. The Bitcoin Lightning Network specification is based on the white paper. The network is being developed by multiple parties including Elements Project, Lightning Labs and ACINQ
Blockchains work as if a computer had to store every mail it receives. The Lightning Network, on the other hand, makes it possible to conduct blockchain transactions and only store the data that users care about – their own token. The network is thus a protocol for scaling and accelerating blockchains. It was designed to solve some of the technical limitations of the Bitcoin blockchain.
The Lightning Network explained in simple terms
In simple words: In order to process transactions faster with the Lightning Network, users do not send transactions to the blockchain, but to the Lightning Network. A Lightning wallet is required for this to work. By sending transactions from the traditional wallet to the Lightning wallet, the transaction can be leveraged on the Lightning Network. After connecting the Lightning Wallet to a node in the Lightning Network, a channel to the Lightning Network opens and a payment channel between the two participants.
We will return to these channels in this article. The transactions in this payment channel are initially not part of the Bitcoin blockchain. Within a payment channel, users can carry out any transactions that are not implemented in the slower Bitcoin blockchain, but in the Lightning Network. Only at the end of all transactions do users transfer their bitcoins from the Lightning wallet back to their bitcoin wallet and thus back to the bitcoin blockchain. This quickly makes it clear that Lightning is particularly helpful in the case of multiple transactions that are carried out between partners at the same time.
The actual bitcoins stay where they are, of course: in the bitcoin blockchain. By using Lightning, the blockchain locks the bitcoins used for further use, and only the equivalent value of the bitcoins is traded in Lightning. After the transactions are completed, Lightning offsets the equivalent value against the actual bitcoins in the blockchain.
The payment channels allow participants to transfer funds without having to publish all transactions on the blockchain. When opening a channel, participants must set an amount. Time-based script extensions such as Check Sequence Verify and Check Lock Time Verify monitor the operations. In a large network of channels in the Bitcoin blockchain, where at least one channel of the blockchain is open, it is possible to create an almost unlimited number of transactions on this network. This makes it easier to send larger transactions, speeds up processes and is also an ideal approach if business partners regularly carry out transactions on the Bitcoin blockchain.
Faster and cheaper transactions
Scalability was the first key motivator for Lightning, as the network’s transaction rate has room for improvement. While the Visa company can process tens of thousands of transactions per second, Bitcoin’s network is limited to fewer than 10 per second.
Another reason for developing Lightning is that the Bitcoin blockchain’s “block confirmation time” is around 10 minutes. This means it takes 10 minutes for the transaction to be confirmed. Of course, this is not ideal for payment transactions. In addition, the fees can be quite high. The Lightning Network, on the other hand, can enable near-instantaneous transactions at rates in the thousands to millions per second and fees as low as a fraction of a cent (or even free).
In the Lightning Network, transactions can be processed in fractions of a second. The use is therefore not only useful for carrying out large and comprehensive transactions, but also interesting for business areas in which transactions have to be carried out very quickly. Instead of 10 minutes, the participants in the transactions only have to wait a few seconds or even less.
Routing Fees
Channels are like pipes — you can send money through them and pay fees along the way. Bitcoin uses a single channel called the blockchain where transactions are stored. Lightning Network does away with the blockchain altogether and creates multiple channels. These channels allow people to make instant micropayments without having to wait for confirmations.
But besides the transaction fees to open or close channels, there is another fee associated with transferring funds between channels. In addition to the transaction fees, each node must pay a small amount of money every time it routes a payment.
The fees for the lightning network could mean that no one wants to route payments because of how much they cost. If that happens, we won’t see many lightning networks popping up around the world.

How do Bitcoin Lightning transactions work?
The network is based on the payment channels already mentioned. A two-party payment channel is created when both parties create a 2-of-2 multi-signature transaction on the blockchain, with at least one party providing funds for the 2-of-2 ledger booking.
Each participant has a private key. The expenses from the ledger posting can only be made if both keys are confirmed. This first transaction to open a channel takes 10 minutes (or whatever the normal block time is). After that, the participants can immediately trade with each other using the bitcoins allocated in the channel. These instant transactions are performed by passing signed transactions back and forth, with expenses being posted from the 2-of-2 ledger.
Every transaction is valid when it is transmitted into the network and recorded in the blockchain by the nodes of the network. In a payment channel, these signed transactions are only transmitted when the participants want the channel to be closed. Transactions signed but not transmitted are exchanged via direct peer-to-peer communication and held by participants like redeemable receipts.
The Bitcoin blockchain aggregates transactions and executes them in blocks for processing. This is different from the Lightning Network. This executes every transaction immediately. The transactions can run across multiple nodes.
Real-world example of channels between multiple participants in Lightning
To use Lightning, two participants, Alice and Bob, create an initial transaction on the blockchain for $20, with each party having $10 of value. The basis is a new payment channel in the Lightning Network. The first transaction is opening the channel and defining the bitcoins that should and can be traded in the payment channel. The bitcoin blockchain locks these bitcoins, so to speak.
The transaction on the Bitcoin blockchain has a multi-signature. The two participants have keys for the transaction carried out. Each participant can send the amount of bitcoins to the other partner that he has defined and owns for the channel as part of the first transaction in the bitcoin blockchain.
This initial allocation can be updated so that Alice gets $5 of the $20 total and Bob gets $15. These transactions now take place initially in the payment channel. That means the processes are faster and cheaper than in the Bitcoin blockchain. The bitcoins that Alice and Bob want to trade with Lightning in this example are locked in the bitcoin blockchain by the first transaction. There is no limit on the number of transactions.
These actions take place outside of the blockchain, within the Lightning Network. When the participants have completed their transactions, the last exchanged transaction signature is sent to the network, completing the movement of tokens in the channel – some to one party and (if any) some back to the other. Only the completed, last transaction can be seen on the Bitcoin blockchain. All other transactions remain in the blockchain. The two participants in the channel can send the amount of blocked blockchain back and forth as they wish. All actions remain in the Lightning Network.
Transactions are also possible in Lightning with more than two parties
This quickly makes it clear how the Bitcoin network is relieved. All transactions between Alice and Bob are not processed through Bitcoin, but in the Lightning Network. This saves enormous amounts of resources in the Bitcoin blockchain, which are available for other transactions, for example. At the same time, the participants benefit from a significantly faster processing of transactions, especially when not just one transaction is to be processed, but several.
Lightning takes the technology behind the payment channels and creates a network of these channels, using smart contracts to ensure that the network can function in a decentralized manner and without counterparty risk. As an example, Alice can open a channel with Bob, who has a channel with Carol, who has one with Dave. If Alice wants to do business with Dave, she can send tokens through Bob and Carol and Dave will eventually receive them. But due to the multi-signature and smart contracts inherent in Lightning’s design, Alice doesn’t have to trust Bob and Carol as an intermediary – the protocol uses cryptography to ensure that the tokens either get to Dave via Bob and Carol, or to Dave automatically Alice to be refunded.
A common mesh network is also created in which transactions outside the blockchain can be implemented quickly. There does not have to be a direct connection to the participant in the channel with which another participant wants to carry out transactions. It is sufficient if each participant has a different channel and the connection can be established via the different channels. These transactions are covered by the individual bitcoins that exist between the channels.
With the peer-to-peer network it is therefore possible to send bitcoins between the participants. In this case, only the two participants in the channels carry out transactions directly with one another, which are also connected to one another. For example, if Alice has a channel with Bob and Bob has a channel with Mike, Alice can trade with Mike. However, Alice trades first with Bob and then Bob with Mike to complete the transaction between Alice and Mike.
Here, only the maximum amount of Bitcoin that is available between two participants in a channel can be sent. In this example, if Alice wants to send a bitcoin to Mike, but Bob only has a half-bitcoin connection with Mike, then Alice can only send that half-bitcoin, regardless of how many bitcoins she has anchored in the channel with Bob.
When a payment channel is closed, the bitcoins are written back to the blockchain, since the Lightning wallet in turn transfers the bitcoins back to the respective wallet.
Disadvantages and problems with Lightning
In order to be able to use the Lightning Network, users not only need a wallet for Bitcoin, but also a wallet for Lightning. At the same time, these wallets must be linked in such a way that transactions are possible between the wallet and the Lightning wallet.
The network cannot be used with conventional wallets, but only with compatible ones. Of course, this does not make it easier for users to use bitcoins. Added to this is the effort involved in opening up new payment channels. Unfortunately, this is still not very user-friendly.
Lightning nodes must be online at all times for Lightning to work. Closing a channel takes some time so that the two participants can be informed in time. A permanent connection to the network is required to avoid fraud.
Liquidity in Lightning only works if all connected participants within the route also have sufficient liquidity. This problem resolves over time as more participants join the network. That doesn’t change the fact that Lightning is a huge benefit of Bitcoin and a solution to the blockchain’s apparent scaling problem.
This exchange risk exists because the business might be paid by their customers in a fiat currency and not Bitcoin.
How many transactions can bitcoin process per second?
An often-recited metric when discussing the functionality of Bitcoin is transactions per second. A block in Bitcoin can be a maximum of 1 megabyte in size. An average transaction is 400 bytes in size. This means that on average 2,500 transactions fit into one block. A new block is found approximately every 10 minutes. Consequently, the Bitcoin system can process approximately 4 transactions per second.
How many transactions per second can the Bitcoin competition?
To get some perspective on Bitcoin’s capacity, let’s compare transactions per second to two attractive alternatives; Visa and PayPal. While the Bitcoin blockchain reaches its limit at more than four transactions per second, PayPal can process up to 115 transactions per second. Market leader Visa even makes 2,000 transactions per second without any problems, and 4,000 transactions at peak times. According to Visa, however, it can do much more: up to 56,000 transactions per second should be possible. How can Bitcoin compete and become a global payment system?
However, two nuances also need to be mentioned in this discussion: the transaction size and the finality of a transaction.
In Bitcoin, it doesn’t matter to the fees and the network whether an amount of 0.001 BTC or 10,000 BTC is sent. What matters is the number of inputs and outputs of the transaction. With alternative payment systems such as Visa and PayPal, you usually pay a percentage of the transaction amount instead. Sending large amounts is correspondingly expensive.
The finality of the transaction describes the possibility that the transaction can be reversed. This is very difficult with Bitcoin: once a transaction has been sent and written to a block, it can hardly be undone. This is an advantage, because sellers can be sure that the supposedly friendly customer will not cheat them afterwards. This is different with PayPal and Visa: here there is a period (usually 30 to 120 days) in which the payment can be revoked. This is possible because PayPal or Visa are the central authority in the monetary system. You determine the history of the transactions and can also change them later.
So while Bitcoin is lagging behind in terms of transaction frequency, the technology can already score massively in terms of transaction size and financial finality.
Payment Channels – The basis of the Lightning Network
The core of the Lightning Network are payment channels. A payment channel can be thought of as a tunnel between two parties, Alice and Bob. So it connects Alice and Bob directly to each other. The difference between a payment channel and a transaction on the blockchain is that payments within the tunnel are not recorded on the blockchain. Instead, Alice and Bob can keep updating the status of the payment channel and only write the last status to the blockchain when they are “done”. The payment channel is updated outside of the blockchain and is not bound by its limitations. Alice and Bob could update their channel status several times per second. In other words, micro-transactions are not only possible, but also plausible.
So if you want to understand the Lightning Network, you should first understand payment channels.
One-way payment channels
The classic channel or payment channel consists of two participants (peers), Alice and Bob. The multi-signature technology Bitcoins and a so-called lock time are used for the channel. Multisignature transactions can be used to generate transactions that require more than one private key to sign a transaction. In the case of payment channels, so-called 2-2 multisig transactions are generated. This means that the bitcoins associated with this transaction require the consent of both parties in order to be sent. The lock time ensures that the coins within the multisig cannot be transferred for a certain period of time.
A unidirectional payment channel only ever sends money in one direction. So from A to B, not the other way around.
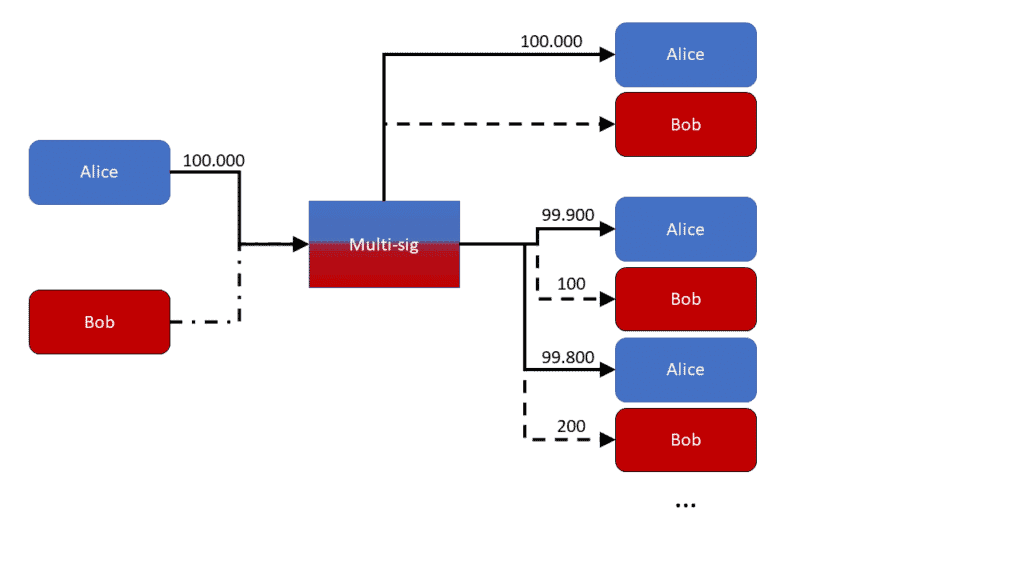
Let’s use a real-world example to illustrate this: Bob runs a coffee shop where Alice buys coffee every morning. So that Alice does not have to write a transaction to the blockchain every time, which takes a relatively long time and costs a lot. Therefore, she opens a payment channel with Bob. It sends a certain amount, in our example 10,000 satoshi, to a 2-2 multi-sig address. Alice controls one private key and Bob controls the other. For a valid transaction to be written to the blockchain, both Alice and Bob must sign the transaction.
The transaction that opens the payment channel is also called a funding transaction . It is written and minded in the blockchain. The funding transaction indicates the maximum amount of money that can be spent.
In addition, Alice brings in a second transaction that automatically sends the 10,000 satoshi back to her address after one month. This is your insurance. So if there are problems with Bob, Alice will get her money back after a month. So Bob could “hold the 10,000 satoshi hostage” for a maximum of one month—not forever.
On the one hand, Alice has now opened a payment channel to Bob, on the other hand, she has a guarantee that she will get her money back in a month at the latest. How does this payment channel work now?
When Alice comes to Bob’s coffee shop in the morning, she has 10,000 satoshi in the payment channel and Bob has zero satoshi. Alice pays for her coffee by updating the channel status. To do this, she creates a transaction within the multi-sig wallet that would only send her 9,000 satoshi and Bob 1,000 satoshi. She signs this transaction and sends it to Bob. Bob now has a signed transaction from Alice for the 2-2 multi-sig wallet. That means he could decide to add his signature as well and then write this transaction (9,000 satoshi to Alice, 1,000 to Bob) in the blockchain. However, he doesn’t do that because he knows that Alice will be back tomorrow. The certainty that he already has a signed check from Alice is enough for him.
The next morning, Alice comes back to the store to buy coffee. Again she pays through the payment channel. So, she creates a new transaction in the multi-sig wallet, which now only sends her 8,000 satoshi and sends 2,000 satoshi to Bob. She signs this transaction and hands the metaphorical check to Bob. This incremental update can continue until the locktime expires. Or until Alice runs out of money left in the channel to spend.
The term “off chain” is also explained in this context. Alice pays Bob with bitcoin, but these payments don’t touch the blockchain directly. They happen outside the blockchain (off chain).
So the advantage is that Alice can buy her coffee every morning. She doesn’t do this with a transaction on the blockchain, but with a check for Bob, which he can cash at any time. Before that, Alice has to top up a kind of pre-paid account from which she can then deduct the individual transactions. When Bob cashes the check, or when the lock time expires, the payment channel is closed. A transaction is written to the blockchain and distributes the remaining money to Alice and Bob accordingly.
There are only two transactions in the blockchain. Once the transaction that financed the multi-sig wallet and once a transaction that closes the payment channel. But between those 2 transactions on the blockchain, a million or more small transactions could have happened between Alice and Bob.
If a payment channel is closed, this is referred to as a settlement transaction . The settlement transaction is written and minded on the blockchain.
So far, however, we have only considered a unidirectional payment channel. So if Alice only sends money to Bob (like when buying coffee). But if the whole thing is also supposed to work in the other direction, things get a little more complicated.
Commitments – When channels should go both ways
A two-way payment channel is a channel where money can flow in both directions.
However, these payment channels must also be established “trustlessly”. That is, neither party can gain anything from cheating and no third party arbitration is required.
For example, one scenario would be that Bob writes an old state of the payment channel to the blockchain. If Alice had already accepted the payment in the payment channel and had given Bob a good or service, she would have been cheated of her money. Of course this must not happen. Therefore, bidirectional payment channels require an extra step. Cryptographic protection must be established for both parties so that participants cannot revert to old payment channel states with impunity.
Recap – additional information] Why is this scenario not a problem with unidirectional payment channels? In the one-way payment channel, only Alice pays Bob money. In return, she hands Bob a check signed by her with the current status of the channel. At no point does Alice receive a signed check from Bob. This means that she cannot make a transaction from the multi-sig wallet, which requires two signatures. Bob, on the other hand, only ever gains more money with new transactions. Out of economic self-interest, he would not write an old state to the blockchain, as this would mean he would receive less Bitcoin than Alice actually wrote over to him. So in one-way payment channels, it’s always best for Bob to post the latest.
Bidirectional payment channels are structured and secured as follows:
Alice and Bob want to establish a two-way payment channel. To do this, the two parties must first agree on an opening transaction (funding transaction) with the respective amounts. So how much each pays into the channel. In our example, Alice deposits 10,000 satoshi and Bob deposits nothing. Alice sends the 10,000 satoshi to a 2-2 multi-sig wallet. For this wallet, Alice has one key and Bob has the other. Both must therefore sign for a valid transaction on the blockchain. If Bob disappears, Alice can get the money back after a certain time.
Now Alice wants to use the payment channel and send Bob 1,000 satoshi. A second multi-sig wallet comes into play for this. After the funding transaction has taken place, Alice creates a new transaction where they send 9,000 satoshi to an address she controls and 1,000 satoshi to the new multi-sig wallet. Two signatures are again required for this new multi-sig wallet. One belongs to Alice, the other is a temporary new address for Bob. In addition, this transaction has a time lock, so it can only be spent after an elapsed period of time. So far so good. Bob could now decide to sign with his temporary signature and thus close the payment channel. Or he waits for the next update of the payment channel.
Bob now wants to send 500 satoshi to Alice via the same channel. To do this, he must reveal his previous signature by sharing the associated private key with Alice. He then creates a new transaction where Alice gets 500 satoshi and 500 satoshi still goes to Bob. For this transaction, a temporary, new signature is required from Alice and a signature from Bob. This transaction is again time locked so Bob gets his full 1,000 satoshi if Alice doesn’t respond.
However, since it is a two-way payment channel, a step must be taken before the commitment transaction. You have to come up with the secret, the pre-image, and exchange it.
In practice, the wallet does this and the user does not notice much of the process. In general, however, you can imagine it like this. The wallet application generates a random, large number. This is the pre image. Then the wallet application hashes the pre image. That’s the hash. Before the payment channel can really get going, both participants create such a pre-image and the associated hash. They exchange this hash with each other. Now everything is ready for the two-way payment channel.
Alice now sends Bob 10,000 satoshi by again signing a check to the multi-sig wallet. This check pays her 49,990,000 satoshi and Bob pays 50,010,000 satoshi. It is therefore a commitment transaction. But this transaction is special because it is provided with a hashed timelock contract. That means Alice uses the hash that Bob gave her and says “whoever can prove that they know the pre-image for this hash can resolve the HTLC.” The other possibility of making a transaction is that a certain period of time elapses . With an HTLC, this time is given in blocks (a block lasts about 10 minutes).
Bob can get his money at any time. To do this, he resolves the payment channel in a settlement transaction by presenting his pre-image in the transaction. Alice can’t do that because she doesn’t know the pre image. Should Bob not cooperate with Alice and try to “hold” the money hostage, he can only do so until the time lock expires. If he hasn’t closed the channel and claimed his money by then, Alice can get all her money back.
If the balance in a payment channel is changed, i.e. one party gives up more Bitcoin, this is also referred to as a commitment transaction . Commitment transactions are not written to the blockchain.
Lightning Network – Channels become a network
Now we understand the technical basics for the Lightning Network. But how does it come from a bidirectional payment channel between Alice and Bob to the network between all participants?
A Hashed Timelock Contract (HTLC) is a class of transaction that must meet a specific condition in order to be valid. More specifically, the sender must either provide cryptographic proof or wait until a specific date.
The HTLC consists of two components, on the one hand the secret (Secret) and on the other hand a time lock. The secret is a random number hashed using a hash function. The initial number used to create the hash is also called Pre Image .
The Pre Image is a random number that serves as a secret for an HTLC. Anyone who knows the pre-image for an HTLC has the cryptographic proof to make a transaction.
Previously, participants would have to set up a new channel for each new payment activity. So if Alice wants to do business with Carol, both business partners would have to set up a payment channel. This is where the Lightning Network comes in – payments could be routed through the individual participants. Instead of Alice creating a new channel with Carol, she instead uses existing channels between her and Bob and Bob and Carol. In this case, Bob acts as an intermediate step, as a hop , between Alice and Carol.
Lightning Network
The Lightning Network is a routed network of bidirectional, end-to-end payment channels. This means that the participants can send each other payments from channel to channel without having to use an intermediary.
The critical reader is puzzled here: ” For a moment, the money goes from Alice via Bob to Carol – isn’t that exactly the trustee model that wants to replace Bitcoin ?”
The Lightning Network is not a trust-based escrow model. Even if the payment finds its way to Carol via Bob, Bob never has control over Alice’s money. This is made possible by advanced cryptography. Just the mechanism of bidirectional, trustless payment channels, the Hashed Timelock Contracts (HTLC).
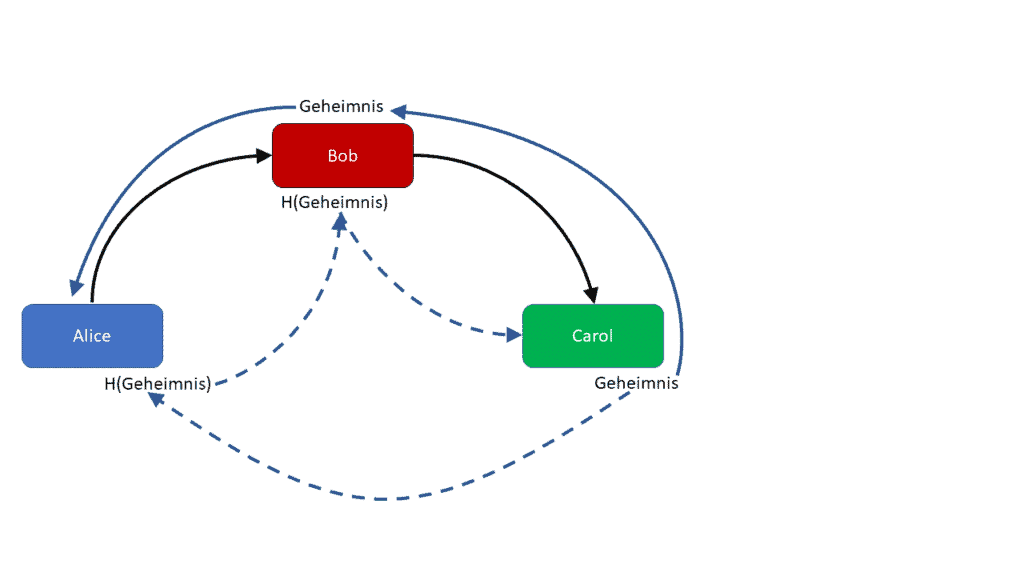
This process guarantees that nobody in the chain of payment channels can cheat, or that cheating does not pay. It works like this: Carol thinks up a secret, again a random number. Carol passes the hash on to Alice. This hash now becomes a pledge: Bob receives a payment if he knows the secret. Alice can check this using the hash. Bob passes on the hash, again promising to pay if the recipient reveals the secret. In principle, the path between Alice and Carol can contain other participants, all of whom use the hash as a pledge. In the figure, only a simple network of three parties has been formed.
HTLCs can be used to connect payment channels between different parties. You can see: Participants in the network, who form a bridge between Alice and Carol as nodes, are the backbone of the Lightning Network. Their importance can be compared to that of the miners on the regular blockchain.
Whoops
The blockchain continues to play a central role in the final settlement of payments and thus for the global consensus. It is secondary whether it is actually the Bitcoin blockchain: The Lightning Network can also interact with other cryptocurrencies such as Litecoin. This is how you can finally realize Atomic Swaps . A channel is opened here, the final settlement of which is stored on different blockchains.
– regardless of whether Carol and Bob have already exchanged bitcoins with each other or not. Peer-to-peer would be skewed to one extreme and thus totally inefficient. One approach would be for participants in different payment channels to pass on transactions. Alice would be able to send money to Carol through Bob. The question is can you trust Bob. On the one hand, he could claim the money and simply not pass it on, on the other hand, Bob’s Lightning Node could fail.
Challenges with the Lightning Network
The practical implementation of the Lightning Network is far from being ready for this technology to be used by a large number of people. The network is currently in an experimental phase. To use it, it is essential to have a healthy understanding of technology. But even then it can lead to the loss of your own Bitcoin. In short: Even if the approach and the idea are already clear, there are still many construction sites.
One of the biggest construction sites – and one of the most frequently mentioned points of criticism against the Lightning Network – is the routing. When a network consists of payment channels, the payment has to find its way through the network. However, the routing method is not specified in the Lightning Network white paper. Lightning Network critics say this is an unsolvable problem. Eventually, new nodes would come online all the time and others would go offline. The mere requirement that you have to be online to receive a transaction deters many from the Lightning Network. So it’s a step backwards instead of forward, because with Bitcoin the recipient does not have to be online to receive payments.
So the technological status of the Lightning Network is still immature. For widespread adoption, the technology must be easy and safe to use. At best, the user does not even notice that he is interacting with the Lightning Network and payment channels. However, it will probably take a few more years before that happens. Last but not least, the experiment could also fail.
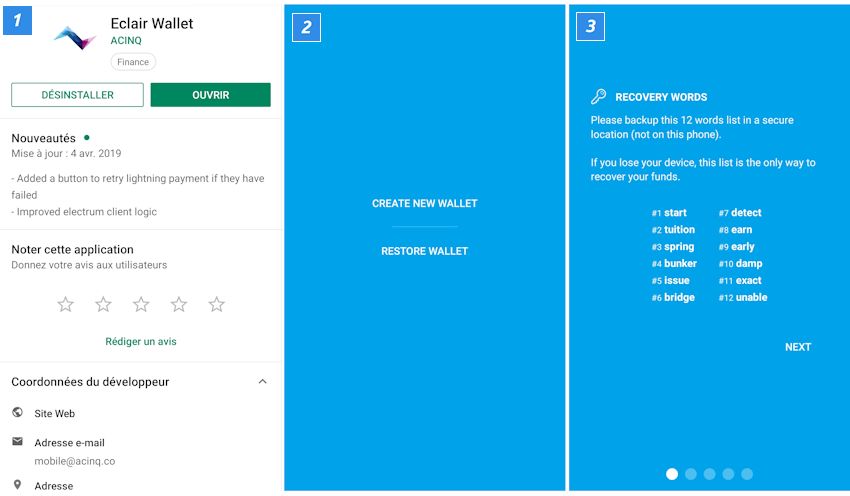
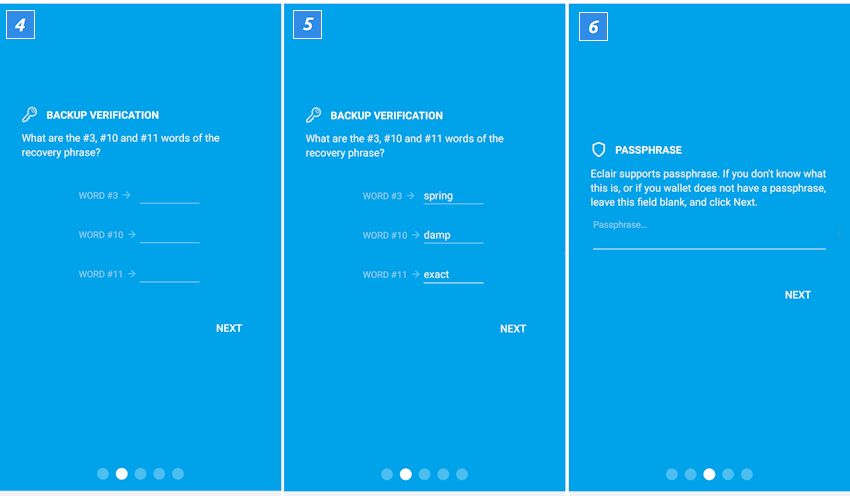
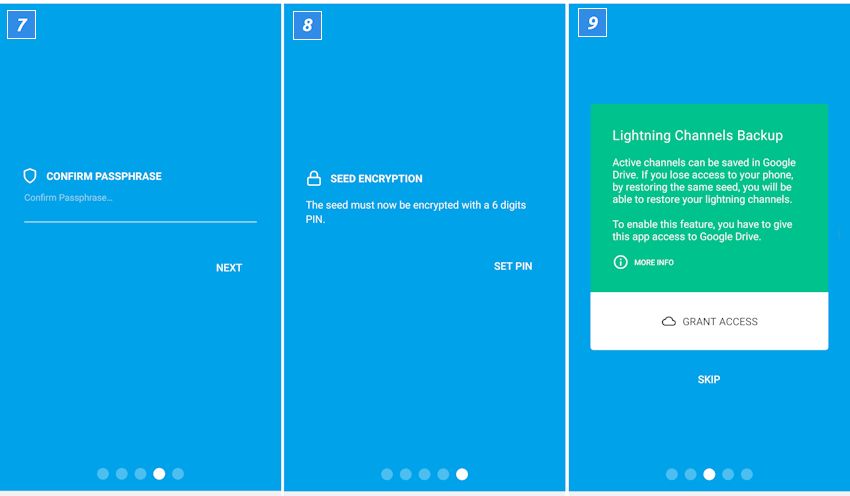
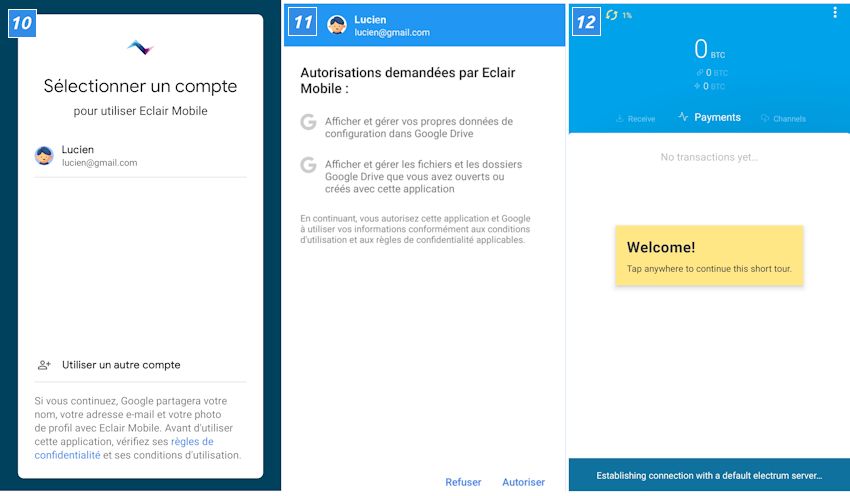
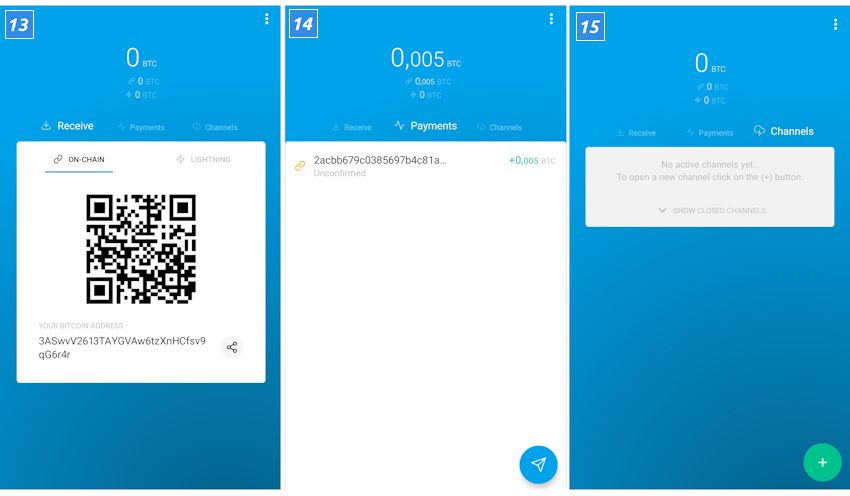
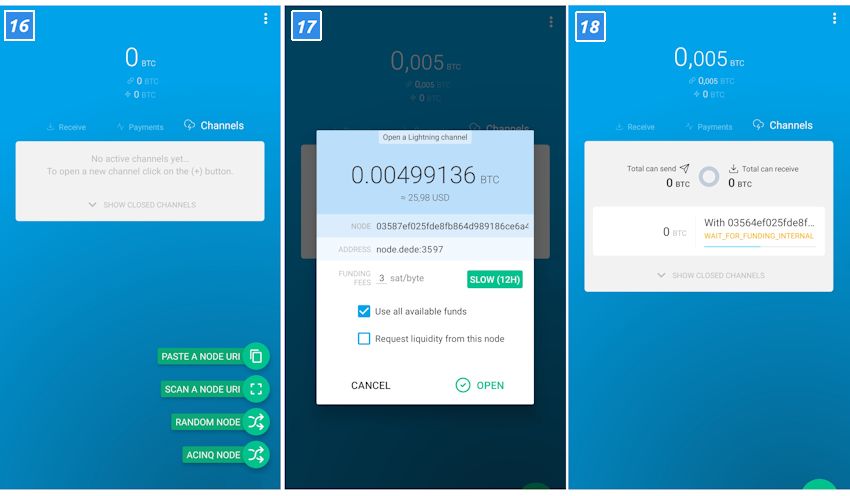
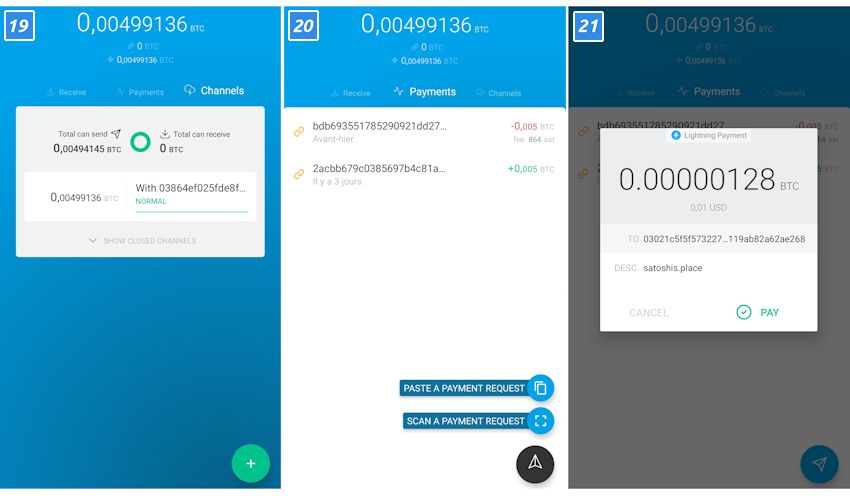
Experience Lightning Network in your own wallet
The Lightning Network is not ready yet. There are now over 2,000 Lightning Nodes. Nevertheless, there is no guarantee that two users can actually set up a payment channel. So there is still a lot to do. True to the motto “Be your own bank”, everyone can help: particularly ambitious ones can set up their own Lightning Node .
The anti-cheat mechanism
” Understanding the Lightning Network is a series of short videos aimed at explaining how Bitcoin’s Lightning Network works. In this fifth episode, we continue our analysis of what really happens behind the scenes when transferring funds from one side of a channel to the other on the Lightning Network. In particular, we go into detail about the mechanisms that make it possible to guard against possible cheating on the part of one’s peer within the channel. ”
Leave a Reply