Category: Tips
-

Safeguarding the Lifelines: A Deep Dive into Critical Infrastructure Protection
In an interconnected world where the functioning of societies relies heavily on complex networks and systems, safeguarding critical infrastructure has become more crucial than ever. This article delves into the realm of critical infrastructure protection, shedding light on its definition, vulnerabilities, and the strategies in place to secure these vital assets. For additional insights, you…
-

HVAC Systems
A. The Role of HVAC Systems HVAC (Heating, Ventilation, and Air Conditioning) systems play a pivotal role in creating a comfortable and healthy indoor environment. They regulate temperature, humidity, and air quality to ensure the well-being of occupants to get carpet cleaning denver. B. The Importance of Proper Maintenance Maintaining HVAC systems is crucial for…
-

The Art of Financial Planning: A Guide to Securing Your Future
The Crucial Role of Financial Planning Financial planning is the cornerstone of a secure and prosperous future. It involves the careful orchestration of your financial resources to achieve your life goals, whether they be buying a home, funding your children’s education, or enjoying a comfortable retirement to get financial advisory. Why Seek Professional Financial Advisory…
-

Hagerstown: A Journey Through History, Culture, and Modern Living
Embark on a journey through Hagerstown, a city that gracefully blends historical elegance with contemporary living. As you step into this captivating tapestry of the past and present, you could try this out for a unique exploration of Hagerstown. This article unravels the architectural marvels, cultural richness, real estate dynamics, and the vibrant lifestyle that…
-
Unlock Your Best Smile: The Dentist’s Secret Tips Revealed
A captivating smile is often considered the key to leaving a lasting impression. Your smile is not just a reflection of your happiness; it also plays a crucial role in your overall health. Achieving and maintaining a dazzling smile requires more than just regular brushing and flossing. For precision and excellence in dental crown procedures,…
-

Protect Your Home from UV Rays with Solar Screen Window Treatments
When it comes to protecting your home, you likely think of locks on doors and windows, alarms, and surveillance cameras. However, one important area that often gets overlooked is protecting your home from UV rays. Not only can UV rays damage your skin and eyes, but they can also fade and damage your furniture and…
-
When Should You Use a Content Services Platform?
Content is the lifeblood of your website and your business. It’s no longer enough to simply have content on your site, you need to manage it in a way that allows you to create, edit, format, and publish as quickly as possible. At its core, this is what enables you to provide a great user…
-
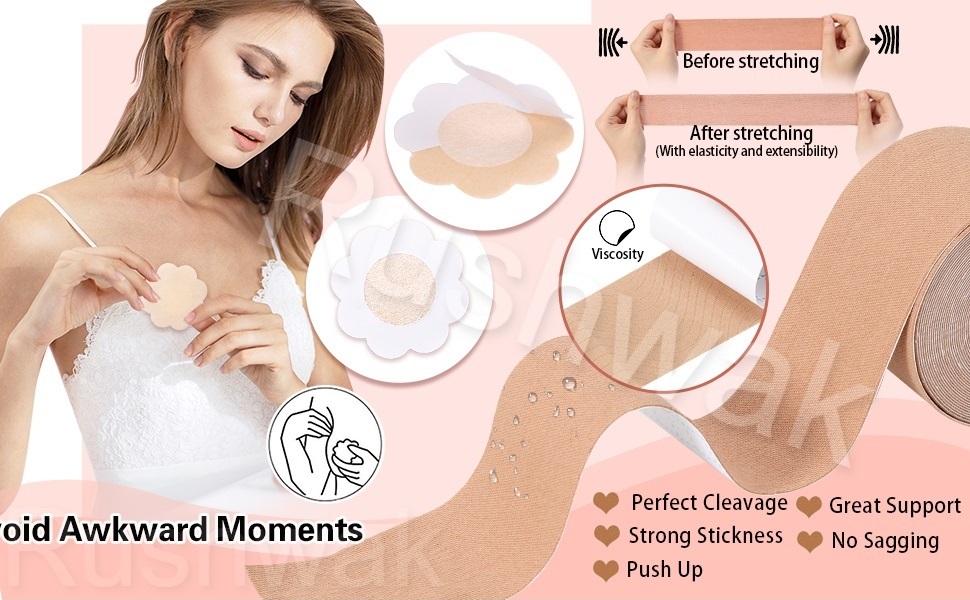
Durable booby tape: the ultimate solution for sagging breasts
Durable booby tape is the ultimate solution for sagging breasts. This versatile and effective product is designed to lift and support the breasts, Buy booby tape nipple cover creating a more youthful and flattering silhouette. Booby tape is made from a strong and durable adhesive material that sticks to the skin without causing irritation or…
-

Top Qualities You Should Seek in a Family and Cosmetic Dentist
Having a healthy, beautiful smile is an important part of life, and at our office, we understand that. At our practice, we provide comprehensive family and cosmetic dentist Austin services to patients of all ages. We strive to provide excellent and personalized care to each patient, no matter their needs. Our experienced, compassionate dentists work…
-

THE 10 BEST REASONS TO BUY A CARAVAN FOR TRAVEL LOVERS
These days, the thrill of taking a family vacation appears more attractive than ever. A new experience to assist you in achieving this is purchasing a Caravan Trader VIC. Since they first appeared in Britain, caravans have undergone significant change. Since the introduction of the first mobile home in 1885, caravans have become extremely popular…