The Zero Trust model provides a way of thinking about security that goes beyond traditional perimeter defenses. Instead of focusing solely on preventing attacks from happening, it focuses on building trust across the enterprise. This approach takes into account every single interaction an employee makes within an organization, whether it involves accessing email, logging onto a network, or even interacting with another person. By looking at each interaction individually, Zero Trust allows organizations to determine what information an individual needs and what actions are required to provide access to that information.
Zero Trust is a relatively new term, but it’s one that we’re seeing gaining traction in the industry as more businesses adopt cloud solutions and expand their workforce over long distances. In fact, Gartner predicts that by 2020, 50% of enterprises will rely on zero trust models to protect sensitive data and prevent unauthorized access.
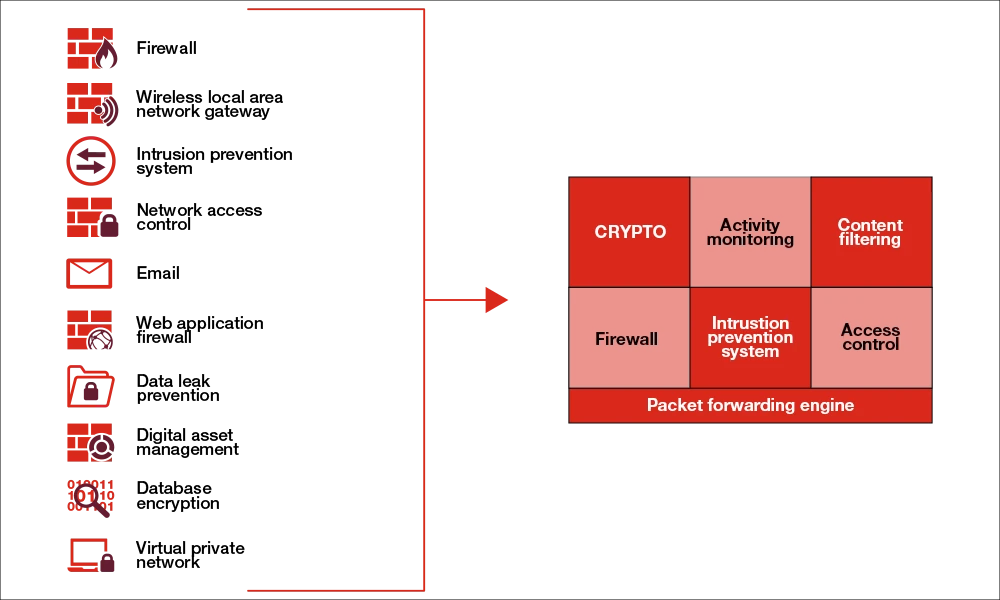
What is the Zero Trust concept?
The Zero Trust concept defines a way to build security into every aspect of a system. This includes network infrastructure, software, databases, and even people.
Zero Trust assumes that every user is untrusted at the start of every single interaction. Systems automatically authenticate and check permissions for a user each time they interact with an app, database, or business resource. Authorization checks continue throughout the use of those assets. If a user attempts to perform an action without proper credentials, they’re denied access immediately.
If you’ve ever been asked to prove your identity online, you know how frustrating it can be. You have to remember a username and password, enter them correctly, and hope you didn’t miss anything else. Zero Trust eliminates that friction by assuming that no one is trustworthy. Instead, systems validate every user’s identity and permission level prior to granting access.
What are the three main stages of the approach?
Zero Trust is a security framework that helps organizations protect themselves against cyberattacks while still allowing employees access to information and applications. To help companies make sense of the concept, we’ve broken it down into three distinct phases. Each phase builds upon the previous ones, and each requires a different set of tactics and procedures.
The first stage involves building trust among stakeholders. This includes educating everyone about what Zero Trust is and how it works. Once the basics are understood, you can move on to the second stage — establishing baseline controls. These include things like network segmentation, secure communications, and application whitelisting. Finally, the third stage focuses on monitoring, detection, response, and recovery.
In our experience, many companies start off with just one of these phases and try to tackle everything at once. While this might work initially, it won’t scale well over time. Instead, consider starting with one of the three stages and moving forward gradually. You find yourself much further ahead sooner rather than later.
1. Visualize the organization
The first step toward implementing a Zero Trust architecture is to understand where it fits within the overall structure of the organization. In some cases, this might require breaking down silos and building bridges across departments.
This visualization exercise is about understanding the connections among the different parts of the organization and identifying the risks involved. It includes mapping out the internal network, determining which systems contain sensitive information, and identifying the people responsible for accessing each system.
2. Mitigate risks and concerns
The third step in the risk management process is to identify and address risks and concerns related to the vulnerability and threat landscape. This includes identifying potential vulnerabilities, threats, and the paths an attacker might take; assessing how well the organization is prepared to respond to each type of risk; and establishing processes and tools that will enable automatic detection of new vulnerabilities and threats. In addition, there should be processes that automatically stop attacks and, when that is not feasible, mitigate the impact of likely outcomes as much as possible. These are known as mitigations.
Mitigation should occur during the discovery phase because it allows you to quickly determine whether a particular attack vector exists and what steps you must take to protect against it. For example, if you find out that a certain file format is being used to deliver malware, you can immediately block access to that file type and prevent the malware from executing. If you discover that a web application contains a flaw that could allow hackers to steal sensitive information, you can immediately patch that hole.
As part of the mitigation phase, businesses should also ensure that their security policies and procedures are up-to-date and effective. They should also make sure that employees know where to go for guidance on handling specific situations. Finally, they should train and educate employees about the latest threats and how to best handle them.
3. Optimize execution
The Zero Trust Framework is designed to help organizations achieve compliance with regulations such as PCI DSS and HIPAA. However, it is important to note that many organizations are already working to meet regulatory requirements and implement security controls. This is why we call the Zero Trust Framework “the next step.”
During Stage 3, organizations will begin to optimize their existing processes and protocols to include additional aspects of the Zero Trust Framework. As the framework expands to cover more aspects of enterprise infrastructures, it becomes increasingly difficult to test every aspect of the system. In fact, some organizations might find themselves unable to complete testing due to resource constraints.
In Stage 4, organizations will focus on optimizing the execution of the Zero Trust Framework across their entire network. They will start to integrate the Zero Trust Framework into their day-to-day operations to make sure that it works effectively and efficiently. At this stage, the goal is to ensure that the Zero Trust Framework is being used throughout the organization, rather than just within specific departments.
To successfully execute the Zero Trust Framework, organizations must prioritize the user experience over everything else. If they don’t, they risk missing critical information about potential threats and vulnerabilities. This could lead to noncompliance and decreased productivity at scale.
Benefits of using the Zero Trust approach
The Zero Trust model is a way to secure an organization while keeping employees productive and happy. It allows you to provide an excellent experience without compromising security, and it provides better visibility into what people are doing online.
A Zero Trust approach uses authentication and authorization methods to ensure that only those who are supposed to see something do. For example, a person needs to authenticate themselves before accessing sensitive information like financial statements. Once authenticated, they must prove their identity and permission to access the information.
This process gives IT teams a much greater level of confidence about what users are doing online. They know who is accessing what resources and when. They can even monitor usage patterns and identify suspicious activity.
In addition to improving security, Zero Trust can help improve employee productivity and satisfaction. People want to work where they feel safe and trusted. When they don’t feel threatened, they’re able to focus on their jobs rather than worrying about cybersecurity threats.
Zero Trust also enables organizations to embrace the cloud. Cloud-based solutions make it easier for employees to access apps and data anywhere, anytime. However, there are risks involved. If your organization doesn’t implement proper controls, hackers could gain unauthorized access to confidential information stored in the cloud.
Using Zero Trust, organizations can mitigate these risks and still keep up with modern technology trends.
Leave a Reply