
In order to be able to trade with Bitcoin, investors first need a so-called Bitcoin wallet, a digital purse. You can find out how to get them here.
The Bitcoin hype is spreading and capturing more and more investors with a kind of gold fever. After all, the price is already scratching the 14,000 euro mark – and many want a piece of the crypto cake. But some people don’t even know how to start or how to buy bitcoins at all.
Before this is possible, however, you first need a Bitcoin wallet. We explain step by step how to do it.
What is a bitcoin wallet?
This is a kind of digital wallet for your digital currency. You can “stow” bitcoins in it or remove some. The Bitcoin Wallet is a special piece of software that allows you to send (sell) and receive (buy) bitcoins.
How does a bitcoin wallet work?
Each wallet consists of a unique character code that is unique to them. The crypto balance is stored in this. The wallet is protected with a password so that nobody but you has access to the wallet . Also, every wallet created is anonymous. In concrete terms, this means that you do not have to enter any personal data . This usually only happens if you then want to register at one of the online trading places such as bitcoin.com.
It is therefore advisable to keep several wallets in parallel in order to divide your credit between them. On the smartphone, for example, so that you can go shopping with it in everyday life, for example. Good to know: Wallets can also be copied and saved like a file. This means that if you have a wallet with a large amount of credit, it is best to also save it offline and store it in various places and secure it.
How do I create a bitcoin wallet?
Since you can own multiple wallets, you must first consider which device you want to use them for. Among other things, you have at your disposal:
- desktop
- mobile
- tablet
On the bitcoin.org website , for example, you can choose between different wallets for a wide variety of systems. So if you choose desktop, you’re going for either
- linux,
- Mac or
- Windows.
Under Smartphone you have the choice:
- android,
- blackberry,
- iOS or
- Windows Phone.
online wallet
You also have the choice between pure online wallets or so-called hardware wallets . The former are web-based wallets that store private keys online on a server, albeit managed by an external party.
This could be a problem for some, after all, the security and control of the Bitcoin holdings are completely in the hands of that external provider . The practical thing about it: all you need for an online wallet is a smartphone with internet access.
hardware wallet
A hardware wallet is a type of USB stick on which the wallet is stored . However, there are only a very small number of them. Nevertheless, they are considered one of the safest ways to store private keys electronically and to make payments. Then select the Bitcoin wallet that suits you. Below are:
- ArcBit
- Armory
- bitcoin core
- Bitcoin Knots
- Bither
- Electro
- Green address
- mSIGNA
How to install a bitcoin wallet
These so-called hot wallets differ only slightly, but are all advertised as easy to handle and particularly trustworthy . Once you’ve picked a wallet, install it and follow the instructions that come with it. As soon as the installation is complete, an icon of the selected provider will appear.
When you click on it, you can usually choose between two functions – create a new wallet or import an existing one. In addition, you often have the opportunity to choose from different versions. You will then receive a ” safety sentence ” which you should write down.
If your computer ever crashes, you can use it to restore the wallet . Tip: Finally, you will find your Bitcoin receiving address under the “Receive” tab . You must always specify this when you buy cryptocurrency.
What actually is bitcoin? Everything about the cryptocurrency in check
Bitcoin is currently on everyone’s lips: But what is actually behind the cryptocurrency? How does Bitcoin work and what can you earn with it?
A year ago, critics would probably not have believed that the cryptocurrency could break the EUR 13,000 mark – but Bitcoin did just that in December. The price has since fallen somewhat, but is slowly recovering.
Bitcoin seems to be gaining more and more public awareness and is also arousing interest among companies. But many are still relatively unfamiliar with the digital currency. So what exactly is bitcoin and how does it work?
What exactly is bitcoin?
As mentioned above, Bitcoin is not a physically printed currency, but a digital means of payment that is created and stored electronically. This process is called ” mining ” or ” digging ” in technical jargon . This means that computers calculate the currency with strong encryption using complicated formulas. On a normal PC and for the layperson, however, something like this can hardly be accomplished – this is why several computers join together to form a network to generate the bitcoins .
Whoever has bitcoins in their possession can use them to purchase goods and services or even carry out financial market transactions, just like with other means of payment . However, what distinguishes Bitcoin from other currencies such as the euro or dollar is its decentralization . No state institution such as the central bank can intervene in the system and control the amount of money or set the framework. The network controls itself.
Who Invented Bitcoin?
A software developer using the pseudonym Satoshi Nakamoto introduced the concept of the digital currency on an internet bulletin board in 2008 and in January 2009 the first 50 Bitcoin blocks were calculated. However, to this day nobody knows exactly who is behind the pseudonym. In the meantime, smart people like Tesla boss Elon Musk have been traded as Bitcoin inventors – but he denied the rumors.
How does bitcoin work?
Bitcoins are based purely on mathematics and can be generated using software. This software is open source software , which means that anyone can understand exactly how it works and whether it serves its purpose.
Behind the Bitcoin is a so-called blockchain technology that arouses great interest in companies and governments. It is also often referred to as a digital account statement, since all transactions that have ever been made are stored in encrypted form in the linked blocks and can be viewed by everyone.
In contrast to other currencies, however, there are no institutions behind the digital currency that stand for value stability. Decisions are made in the Bitcoin network only with a consensus mechanism that is defined by program code.
How do I buy bitcoins?
You can either buy bitcoins with a conventional currency on one of the numerous bitcoin exchanges or you receive them as a means of payment for goods and services that you provide. The best-known online exchange is bitcoin.de.
Anyone who buys bitcoins can either leave them on the exchanges and use them as a kind of online account or buy a digital wallet , i.e. a digital purse that can be installed on a computer or smartphone. Examples are “Ledger”, “Trezor” or “Coinbase”. A Bitcoin address is then stored in this app.
The advantage is that you can open an account at any time without having to provide any proof. In addition, no names or residential addresses are assigned to the accounts, so that you can make your transfers anonymously .
Where can I shop with Bitcoins?
More and more internet shops, but also restaurants, service providers and schools accept the cryptocurrency as a means of payment. In Germany there are now around 160 companies .
How much is Bitcoin worth?
The cryptocurrency has no fixed value, which means that its value is determined by the relationship between supply and demand . In the early stages of bitcoin, it was only worth a few cents – it is currently around 12,000 euros .
However, critical financial experts or representatives of regulatory authorities constantly warn of an enormous crash because Bitcoin is an “object of speculation” or it only has an exchange value that one can only hope will be accepted in the future. However, that is not stopping many Bitcoin prospects from jumping on the bandwagon and getting a piece of the pie for themselves.
What are the advantages and disadvantages of bitcoins?
As already mentioned, Bitcoins bring a number of advantages compared to traditional currencies. These include the following:
- Bitcoins are largely forgery-proof
- they protect the anonymity of the owners
- the value cannot be artificially falsified by the state or banks
- a Bitcoin account can be created without any bureaucratic hurdles
- there are hardly any transaction costs
- Bitcoin payments are processed within minutes and don’t need a middleman like a bank. The transfer takes place without detours and reaches the recipient directly.
Unfortunately , the freedoms that Bitcoin allows also make it unpredictable . The price of the digital currency is still rising, but it is difficult to predict how the cryptocurrency will hold up in the future. This inevitably results in disadvantages:
- no institution can vouch for the stability of value
- the currency cannot be used without a computer
- the anonymity may call operators of shady deals onto the scene
- once a transaction has been made, it cannot be undone
Bitcoin mining: This is how you can easily earn money from the crypto boom
Bitcoin followers are in a gold rush: They mine as much digital money as the computer can handle. But what is mining anyway – and how can you make money from it?
Bitcoin mining is the new prospecting for gold – and if you are a miner, you can make a lot of money with it. All you have to do is turn on your computer. After all, anyone can generally generate the virtual currency themselves. However, this requires a little technical tutoring. You can find out how mining works here.
What is bitcoin mining?
Bitcoin mining provides computing power for processing Bitcoin transactions, backing up data and synchronizing all users in the network. It monitors, manages and records all activities. This makes it a kind of Bitcoin data center from miners worldwide .
In it, all transactions that have taken place within the network within a certain period of time are noted in a list, the so-called block. The miner confirms these transactions and enters them into a virtual “account book” called a blockchain. Whenever a new block is created, it is added to the blockchain.
This is transparent and visible to everyone. However, the person who carried out the transaction always remains anonymous. To ensure data security , the information in each newly generated block is encrypted in the form of a hash – a mere string of letters and numbers.
This makes each hash unique – as soon as just one character in the block is changed, the whole hash changes. However, the hash of one block actually uses the hash of the previous one. This creates a kind of seal of approval that confirms that both hashes are correct and valid. If someone wanted to manipulate a transaction, this would be noticed immediately. At the end the hash is added to the blockchain.
How Much Do I Earn From Bitcoin Mining?
In return, the miner is currently rewarded with around 12.5 bitcoins. This is usually part of the transaction fee. But since the cryptocurrency is limited, there is a risk that all available blocks will soon be converted and all bitcoins will be skimmed off. Therefore, it is intentionally made more and more difficult for users to generate hashes.
What do I need for bitcoin mining?
Actually, an ordinary computer is usually sufficient to be able to take part. However, you also need special bitcoin mining software called Bitcoins Client or Bitcoins Wallet to connect your computer to the network.
However, the computing power is often not sufficient – it is therefore advisable to use special Bitcoin mining hardware or an extremely good graphics card in order to be able to survive in global competition. The former have special ASIC chips installed. According to the Bitcoin portal btc-echo , the best Bitcoin miner is currently the AntMiner S9 from Bitmain. To do this, you have to connect the hardware to a router via a LAN cable and configure the miner via the web browser.
Mining bitcoins using cloud mining
Anyone who chooses this variant rents the required software and hardware from an external company for a financial consideration in a cloud – and the bitcoins mined are credited directly to their own digital wallet (which they set up beforehand) as a percentage.
It should be noted, however, that each provider handles how computing power can be purchased differently. In addition, interested parties should consider that there could be black sheep behind overly tempting low prices or offers.
Mining bitcoins using mining pool
Since you have to assert yourself against large international competition in Bitcoin mining and the process also takes much longer, some miners have already joined forces. In concrete terms, this means that the computing capacity of all users is bundled and the reward in the form of bitcoins is divided among the individual prospectors according to their computing power. But be careful: Finally, make sure that you are dealing with a reputable mining pool if you want to register.
Blockchain, what is it?
“If someone comes to you and asks you, ‘Do I need a blockchain for my business?’ Ask them, ‘Do you need something open, neutral , without borders, that no one controls and that resists censorship? If so, then you need Bitcoin, Ethereum, Monero, or Zcash.[…] If not, if you don’t need any of that, what you’re asking for is a database. Install one, you don’t need blockchain. –Andreas Antonopoulos .
Definition by Stéphane Bortzmeyer:
[a blockchain is] an ordered database (the blocks contain transactions, write operations in the chain, which are in a specific order), distributed over a network (typically the Internet), and which has no manager unique. Each machine, each node, carries the whole chain and destroying it would therefore require destroying tens of thousands of machines, managed by different people. The blockchain is public: anyone can create a node overnight, which will automatically download and verify the chain, along with all the data it contains. Anyone can write to it (often for a fee) and these writings are signed , and are kept eternally in the chain, which is therefore a book of operations, containing all the history. The integrity of the chain is guaranteed by cryptography . Any modification is detectable by all. Please note that I said any modification. The chain does not distinguish between “legitimate” or “illegitimate” modification. Once a transaction is in the chain, it’s there forever, even if you think you have good reason to cancel it.
Asymmetric cryptography (encryption)
In asymmetric cryptography, you don’t work with a single key, but with a pair of keys. Consisting of a public and a private key. These methods are referred to as asymmetric methods or public key methods. The terms public-key cryptography and public-key encryption are also common.
A fundamental problem of cryptography is that the communication partners have to agree on a common key. This is known as the key exchange problem.
While a manual key exchange through a personal meeting or by phone with a handful of communication partners would certainly not be a problem. With many keys or many communication partners, it quickly becomes confusing and time-consuming. This is where the topic of key management and distribution comes into play. Alternatively, there is the possibility of using an authentication server. For example, Kerberos. Alternatively, asymmetric cryptography can be used.
Asymmetric encryption methods work with key pairs. One key is the public key and the other is the private key. This pair of keys is closely related via a mathematical algorithm. Data encrypted with the public key can only be decrypted with the private key. Therefore, the private key must be kept secret by the owner of the key pair.
The concrete use case looks like this: If the sender wants to send encrypted data to the recipient, he needs the public key of the recipient. The data can be encrypted with the public key, but can no longer be decrypted (one-way function). Only the owner of the private key, i.e. the correct recipient, can decrypt the data. It is important with this method that the private key is kept absolutely secret by the key owner. If a stranger gets hold of the private key, the key owner must obtain a new pair of keys.
The problem with asymmetric cryptography is the distribution of the public keys. Typically, the public key is handed over at the first contact. However, this raises the question of whether this key is actually the real key of the communication partner.
Note: Asymmetric methods require much more computing power than symmetric methods. Comparing RSA and AES, RSA is about 1,000 times slower than AES.
One-way function and trapdoor function
Asymmetric encryption involves choosing a function that is very easy to calculate, but whose inverse is very complex. This is realized with modulo arithmetic operations. Some of them are actually very easy to calculate, while the inverse is very difficult. So they correspond to a one-way function. However, there are also functions where the inversion can be shortened with additional information. In such a case one speaks of a trapdoor function.
The discrete logarithm is particularly noticeable here as a one-way function because it can be calculated very easily. Conversely, it is simply not possible to calculate back a large number in a practical time. This is known as the discrete logarithm problem. Many asymmetric methods are based on it. However, this does not mean that at some point a way will not be found to solve the discrete logarithm.
Another one-way function is the multiplication of prime numbers. While multiplication is not a problem for a computer, the reverse route, where the prime product is to be factored, is not feasible in a reasonable amount of time. One speaks of factorization and in this context of the factorization problem.
For example, if you calculate 17 x 19 (both prime numbers), you get 323. And now you should recalculate the two unknown factors (17 and 19) from this. There is basically only one way. You have to try all possibilities. With sufficiently large prime numbers this takes forever. This is the factorization problem.
All common asymmetric methods are based on complex mathematical calculations that have in common that there is no simplification for them yet. Key, plaintext and ciphertext represent large numbers or pairs of numbers. However, the procedures are only secure until someone has found a simplification.
Because there are only a limited number of suitable mathematical calculations with one-way functions, it is not possible to develop any number of asymmetric methods.
Attacks on asymmetric encryption methods
- Public-key-only attack: Knowing the public key, the attacker can encrypt any plain text and, for example, compare it with plain text that has already been encrypted.
- Chosen Cipertext Attack: In this attack, the attacker sends any ciphertext to his target to have it decrypted.
- Shor’s algorithm: prime factorization and calculation of discrete logarithms
How secure is asymmetric cryptography?
All safe asymmetric methods of the last decades are based on the factorization of prime numbers or the discrete logarithm. Methods such as RSA and Diffie-Hellman remain safe only as long as nobody comes up with a trick like factoring in realistic time or solving the Discrete Algorithm Problem.
Even the discovery of a practicable factorization method would mean that the asymmetric methods currently in use are unsafe. That would be a disaster for modern cryptography. The security of much of the telecommunications, computer systems and networks would collapse like a house of cards.
Compared to symmetric methods, asymmetric methods are slow and complex and therefore very susceptible to implementation errors. Complicated mathematical methods, such as those used in asymmetric methods, offer more points of attack and thus more approaches for cryptanalysis. Unfortunately, most security gaps arise from incorrect implementations of cryptographic protocols and from checking the authenticity of the communication partner. In comparison, the common symmetrical methods with their simple bit operations and shorter key lengths are more secure.
For good reason, plain texts are never directly encrypted with asymmetric methods. The danger of a successful cryptanalysis is simply too high. In practice, asymmetric methods are preferably used for encrypted transmission of session keys or hashes.
In practice, the usual cryptographic protocols combine both symmetric and asymmetric methods. The key is exchanged using an asymmetric method and then encrypted using a symmetric method.
Asymmetric encryption methods based on prime factor analysis and the calculation of discrete logarithms can be broken using the Shor algorithm with the help of quantum computers.
What is ECDSA?
ECDSA is the public key electronic signature algorithm used by Bitcoin. It makes use of elliptic curve cryptography . The security of ECDSA relies on the difficulty of calculating the discrete logarithm of a large integer.
Typology of Bitcoin and Lightning nodes
1. Bitcoin nodes
The first versions of the Bitcoin software (later called Bitcoin Qt then Bitcoin Core ) brought together all the features expected of a Bitcoin node: it was a wallet, a miner, a complete archive of blocks and transactions and a trading software. validation and routing. The software definitely ceased to be used as a miner with the development of GPU mining and the tools became specialized. In an article published on July 13, Gloria Zhao proposes to classify Bitcoin nodes into four categories according to the services they provide:
– Validation and archiving nodes : These are full nodes ( full nodes ) that have a copy of the complete history of the transaction register (the blockchain ). These nodes are able to verify, validate, and broadcast incoming transactions and blocks, as well as query block and transaction data from any point in history. They have a crucial role as they allow new nodes to catch up with block history to become full nodes.
– Validation nodes without archiving : These are also full nodes capable of verifying, validating and distributing transactions and blocks but which do not allow the entire history to be downloaded. Instead of searching the database for blocks on every commit, these nodes just pick up the entire UTXOs (unspent transaction outputs). Bitcoin nodes do not necessarily need a full copy of the blockchain. As long as they keep block metadata and all UTXOs up to date they can validate and broadcast new blocks and new transactions. These “pruned” nodes download and process blocks to create the database needed for validation, then discard old blocks to save disk space. Since they have all the necessary information, they can verify and validate new blocks and new transactions, so they are indeed full nodes.
– The writing or mining nodes : These nodes write the new pages and insert them into the register (= they produce the new blocks). This involves checking the validity of transactions awaiting confirmation, gathering them into a block, and winning a proof-of-work contest. To do this, these nodes arrange these transactions in different ways and vary a random value (the nonce) in an attempt to obtain a hash .bouldering below a certain target difficulty. The winning node can then add a new page to the Bitcoin ledger and, as a reward, earns the mining bounty as well as the fees from validated transactions. The computing power required is such that these nodes today operate specific installations (currently ASIC cooperatives). Some mining nodes are full nodes, maintaining a full copy of the blockchain, while others are lightweight nodes that are part of a mining pool and depend on the pool ‘s server full node .
– Thin clients : This expression refers to nodes that do not maintain the state necessary to commit transactions and blocks ( see a list of applications here ) and which trust full nodes to do this work for them . A thin client can keep a limited amount of data in order to verify its own transactions, without validating the blocks. Also known as Simplified Payment Verification (SPV) nodes.
2. Lightning Nodes
All Lightning Network nodes are based on a Bitcoin node. This node allows them to perform channel open/close transactions and monitor the ledger (the blockchain ) to prevent a peer from attempting to steal funds from a channel by posting an old transaction that does not reflect the latest statement of the balance of accounts. We will distinguish:
– The complete “infrastructure” nodes which are permanently connected in order to relay payments from users of the Lightning Network. These nodes are generally public and visible to everyone . There are three different implementations: Eclair from Afive (not to be confused with Eclair wallet ), C-Lightning from Blockstream, and Lightning Network Daemon (LND) from Lightning Labs.
– The complete “end of line” knots , used in particular on smartphones (but not only). These are real Lightning nodes that require opening at least one channel to a public node on the network. These nodes, often intermittent, are however content to send and receive their own transactions without relaying those of others. Neither these nodes nor the channels linked to these nodes are public. The applications that run them allow both Bitcoin onchain transactions (these are also SVP wallets ) and Lightning transactions. We can cite for example Eclair wallet , Zap or Electrum .
– Partial nodes that leave full ownership of funds to users but depend on an external server or node to operate. We will mention BLW (Bitcoin and Lightning Wallet) or Phoenix which has the particularity of making the creation and closing of channels invisible for a better user experience (for a few additional costs).
We will not consider LN custodials applications as nodes, since users rely on the “infrastructure” node of the third party to which they entrust their funds. Let us mention all the same in this category: BlueWallet , Wallet of Satoshi or tippin.me
How bitcoin mining works
Newly initiated transactions are attached to the blockchain with the help of the miners . To do this, the miners summarize transactions from a certain period of time and try to create a new block. This new block is created via a special consensus process. In the case of the Bitcoin blockchain, a cryptographic task must be solved to create the new block. To do this, the miners use the SHA-256 hash function, among other things .
The following three quantities serve as input for the task:
- the previous hash (256 bit): the most recent block of the blockchain as a starting point.
- the Merkle Root : a value generated by pairwise “hashing” the transactions to be weaved in using a Hash Tree / Merkle Trees. The last hash value is the root hash / Merkle Root.
- die nonce : arbitrary value to ensure that a solution can be found (variable by which the task must be resolved).
According to the Bitcoin protocol, the output must be a new hash with the first 17 bits set to zeros. This new hash can only be found if the miner computers keep trying and exchanging the nonce until the task is solved. This extremely computationally intensive consensus process is called “Proof-of-Work” (PoW) .
The miner who calculates the new hash first publishes the block on the network. At this moment, the nodes involved in the blockchain check whether the newly created block is valid. This is the case when the input sizes used (“Previous Hash” and woven-in transactions) together with the selected nonce result in the new hash value with x leading zeros. Checking this fact – i.e. recalculating the solved task – only takes a fraction of a second, whereas finding a solution can take several minutes.
Miners are used to maintain the network deployment of computing power and generation of new blocks. The miner who creates the next block first receives, among other things, a protocol-based reward of currently 12.5 Bitcoin.
–
Virtual currencies such as bitcoins are increasingly becoming the focus of public interest. They work on the basis of blockchain or distributed ledger technology. Volker Brühl explains how they work and shows that these technologies can not only revolutionize the financial sector.
Bitcoins and other so-called virtual currencies or cryptocurrencies are increasingly being targeted by supervisory authorities, as they can be kept anonymously, transferred or exchanged for classic currencies and are therefore suspected of facilitating money laundering as a result of illegal transactions. The European Banking Authority (EBA) has repeatedly pointed out the risks of cryptocurrencies. On May 20, 2015, the fourth European Money Laundering Directive (EU 2015/849) was passed, which initially did not cover virtual currencies. However, on July 5, 2016, the EU Commission proposed including operators of exchange platforms and providers of electronic wallets for virtual currencies in the provisions of the 4th Money Laundering Directive. This would largely eliminate the previous anonymity of users of virtual means of payment. The short-term extension of the 4th Money Laundering Directive makes it clear on the one hand how high the need for action is estimated on the political side. On the other hand, critics fear that stricter regulation of cryptocurrencies will jeopardize the development of an innovative market segment in Europe.
The blockchain technology underlying bitcoins and most other cryptocurrencies, which is based on the principle of a distributed ledger with transaction accounts (distributed ledger), is credited with the potential to not only revolutionize the financial sector, but also to trigger disruptive changes in other industries too be able. In the public discussion, bitcoins, blockchains and distributed ledgers are often not sufficiently differentiated. Therefore, in the following, the functionality, market developments and the ecosystem of virtual currencies will be explained using the example of bitcoins. The potential fields of application for distributed ledger technology are then outlined.
Bitcoins and blockchain at a glance
Blockchain technology was originally developed as a platform for launching so-called “virtual currencies”. Bitcoins or other cryptocurrencies are not money, but accounting units that can be used as a means of payment in multilateral clearing circles on the basis of private-law agreements without requiring approval from the supervisory authorities. However, extended services such as the brokerage of purchases and sales or the operation of trading platforms may be subject to approval.
With cryptocurrencies, electronic payments are processed directly between senders and recipients without the need for a financial intermediary (e.g. a bank). These web-based payment transaction systems use methods of cryptography (encryption technology) in order to be able to process transactions securely and inexpensively with the help of a distributed computer network (so-called peer-to-peer networks). Although the algorithms of the respective cryptocurrencies differ in many details, the transaction processes are largely based on similar basic principles, which are explained below using Bitcoin as an example.
Bitcoin is the first and so far the most widely used cryptocurrency. The associated reference software was published in 2009. All transactions with bitcoins are mapped in a distributed database and combined into blocks and linked together in such a way that a complete and forgery-proof sequence of transaction blocks (the so-called blockchain) is created. All transactions of the blockchain can be viewed by every participant in the network. However, outsiders cannot see who actually owns the virtual monetary units. Transactions, once made, are irreversible. Bitcoins are not created in a classic money creation process through the interaction of monetary policy instruments of central banks, commercial banks and bank customers, but with the help of a defined incentive system that rewards those participants in the payment network with new monetary units who check the authenticity of encrypted transactions particularly quickly with the help of mathematical algorithms. This process of validation and the associated generation of new units of cryptocurrencies is called mining. Bitcoins and other cryptocurrencies are therefore based on the trust of the participants in the integrity and security of a decentralized computer network and not on the credibility of a central bank. While neither the central bank money nor the creation of book money are subject to quantitative limits in traditional monetary systems, the maximum number of units of artificial currencies that can be generated is usually limited by the system. which rewards those participants in the payment network with new monetary units who check the authenticity of encrypted transactions particularly quickly using mathematical algorithms. This process of validation and the associated generation of new units of cryptocurrencies is called mining. Bitcoins and other cryptocurrencies are therefore based on the trust of the participants in the integrity and security of a decentralized computer network and not on the credibility of a central bank. While neither the central bank money nor the creation of book money are subject to quantitative limits in traditional monetary systems, the maximum number of units of artificial currencies that can be generated is usually limited by the system. which rewards those participants in the payment network with new monetary units who check the authenticity of encrypted transactions particularly quickly using mathematical algorithms. This process of validation and the associated generation of new units of cryptocurrencies is called mining. Bitcoins and other cryptocurrencies are therefore based on the trust of the participants in the integrity and security of a decentralized computer network and not on the credibility of a central bank. While neither the central bank money nor the creation of book money are subject to quantitative limits in traditional monetary systems, the maximum number of units of artificial currencies that can be generated is usually limited by the system. which check the authenticity of encrypted transactions particularly quickly using mathematical algorithms. This process of validation and the associated generation of new units of cryptocurrencies is called mining. Bitcoins and other cryptocurrencies are therefore based on the trust of the participants in the integrity and security of a decentralized computer network and not on the credibility of a central bank. While neither the central bank money nor the creation of book money are subject to quantitative limits in traditional monetary systems, the maximum number of units of artificial currencies that can be generated is usually limited by the system. which check the authenticity of encrypted transactions particularly quickly using mathematical algorithms. This process of validation and the associated generation of new units of cryptocurrencies is called mining. Bitcoins and other cryptocurrencies are therefore based on the trust of the participants in the integrity and security of a decentralized computer network and not on the credibility of a central bank. While neither the central bank money nor the creation of book money are subject to quantitative limits in traditional monetary systems, the maximum number of units of artificial currencies that can be generated is usually limited by the system. This process of validation and the associated generation of new units of cryptocurrencies is called mining. Bitcoins and other cryptocurrencies are therefore based on the trust of the participants in the integrity and security of a decentralized computer network and not on the credibility of a central bank. While neither the central bank money nor the creation of book money are subject to quantitative limits in traditional monetary systems, the maximum number of units of artificial currencies that can be generated is usually limited by the system. This process of validation and the associated generation of new units of cryptocurrencies is called mining. Bitcoins and other cryptocurrencies are therefore based on the trust of the participants in the integrity and security of a decentralized computer network and not on the credibility of a central bank. While neither the central bank money nor the creation of book money are subject to quantitative limits in traditional monetary systems, the maximum number of units of artificial currencies that can be generated is usually limited by the system.
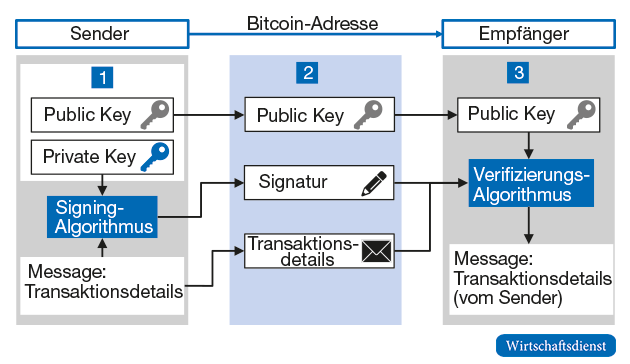
Process of a bitcoin transaction
Each participant in the Bitcoin network must have the appropriate software (wallet) that provides access to the Bitcoin reference software and enables transactions to be carried out. There are a variety of different wallet solutions that differ primarily in whether they only enable the basic function of managing Bitcoin addresses and their own transactions or whether they enable the user to replicate a complete Bitcoin client. Figure 1 illustrates the basic process of a bilateral Bitcoin transaction.
- The sender first generates a “key pair” consisting of a private key and a public key. The private key is used by the sender to generate an encrypted signature, the public key is used by the recipient and the entire Bitcoin network to verify the signature and thus to check the legitimacy of the sender. To transfer bitcoins, you need the recipient’s bitcoin address. Bitcoin addresses are combinations of characters with up to 34 digits that are generated using cryptographic processes. Unlike accounts, bitcoin addresses are typically used only once for a transaction for security reasons.
- The sender of bitcoins then generates a transaction that has to be generated according to a specified format and, in addition to the destination address, contains, among other things, the amount and the transaction references to all previous bitcoin transactions that identify the sender as the rightful owner of the bitcoins to be issued. The private key then uses a signing algorithm to create a signature for the data, which is then encrypted and sent to the recipient via the Bitcoin network together with the public key.
- The recipient can now use the sender’s public key to verify the transaction, ie check whether the sender actually sent the bitcoins to the recipient and whether the recipient is the authorized owner of these bitcoins. Because the signature can only have been created by the owner of the private key that matches the public key sent.
The principle of the blockchain
At the same time, new transactions are sent to all network nodes, which in turn check the validity of the transactions decent rally and, if necessary, try to combine them into a new block and add them to the blockchain. In order to ensure that all network nodes always have the same status of the blockchain and are given an incentive to continuously verify the validity of the individual transactions and ultimately the blockchain as a whole, an incentive system for generating new blocks is required. This is done with the help of the so-called mining process, which provides that a mathematical problem has to be solved in order to create a new block.
In order to create a new block, an encryption value (so-called hash value) of the “block header” must be created using a cryptographic function that falls below a specific target value.
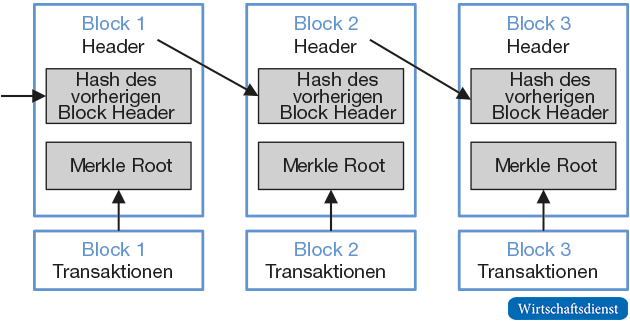
Figure 2 shows a simplified representation of the blockchain. Each block has its own encryption score, which is derived from the encryption scores of each transaction in the block and the reference to the previous block. This creates a linear concatenation of the blocks to form a blockchain. The respective hash values are generated by so-called hash functions, with which any character strings are transformed into seemingly random character strings according to predefined algorithms. A popular hash function that is also used by the Bitcoin system is the SHA 256 function, whose output consists of hexadecimal sequences with a length of 256 bits. Even small changes in the output data lead to unpredictable changes in the output data.
Each block contains several new transactions that are stored in the transaction part of the block. Copies of the transactions are then encrypted, i.e. “hashed”, first individually and then in pairs until a single hash value remains. This is also referred to as the “Merkle Root” of the “Merkle Tree” consisting of the transactions. The Merkle Root is stored in the block header. The block header also contains the hash value of the previous block header and a dedicated NONCE (Number Only Used Once) field. The miners now have to use an algorithmic search process to search for random numbers for the NONCE field until the hash value of the new block falls below the required target size. NONCE can only be used once to make future forgery more difficult.
The newly generated block, including the transactions it contains, is then sent to all network nodes, which in turn can then verify the validity of the block and, if necessary, add it to the blockchain as a new element. If competing miners form a new valid block almost simultaneously, temporary forks can arise in the blockchain. However, these quickly resolve as the network always agrees on the longest block. A distributed transaction ledger is created that contains a complete, immutable history of bitcoin ownership and transfer relationships. Although this register is public, it nevertheless enables the confidentiality of individual transaction details, as these can only be viewed with the respective private key of the authorized person.
The cryptographic chaining of transactions and blocks means that not a single transaction can be changed without also changing the block as a whole and all subsequent blocks. The proof-of-work concept thus prevents historical transaction and block data from being easily altered. Because a potential hacker would have to have more than 50% of the computing power of the entire network to be able to manipulate transactions ex post. This would involve enormous costs, but is theoretically possible.
Since the miners guarantee the authenticity of the transactions contained in it and indirectly the entire blockchain when creating a new block, the miners receive a reward in the form of a certain amount of new bitcoins (BTC). This is halved every 210,000 blocks, so that the maximum amount of Bitcoins that can be generated is 21 million. Neither the absolute amount of the mining fee nor the underlying halving algorithm or the selected adjustment period are comprehensibly justified by the Bitcoin developers. When the bitcoins were introduced, the mining wage was still 50 BTC, which was then halved to 25 BTC for the first time in November 2012. Since July 2016, 12.5 BTC have been distributed to miners per block. On September 15, 2016, around 15.8 million BTC were in circulation.
The lower the target value is set, the greater the average computational effort that must be expended in order to determine the corresponding target hash value for a new block. The difficulty level of the proof-of-work is adjusted from time to time in the Bitcoin Core as the processing power of the Bitcoin network increases over time. The level of difficulty is calibrated by the Bitcoin Core in such a way that a new block is generated every ten minutes on average.
Other art currencies
Since bitcoin was invented, there have been a number of attempts to mimic the concept using different encryption technologies. There are now more than 700 such artificial currencies, but only 16 of them have a market capitalization of more than $20 million (as of the end of October 2016). The top three include Ethereum, Ripple and Litecoin:
- Ethereum : The Ethereum platform was only released in mid-2015. In contrast to most other cryptocurrencies, Ethereum offers users the option of mapping so-called “smart contracts” in the Ethereum blockchain in addition to its own artificial currency, ether. Smart contracts are contracts in which rights and obligations, conditions and consequences are structured digitally in algorithms in such a way that they can be implemented as applications on blockchain technology. The monitoring of compliance with the contractual agreements (monitoring) as well as the automatic initiation of consequences in the event of corresponding violations (self-execution) are fundamentally possible.
- Ripple: With “Ripple”, the US company Ripple Labs has developed a technology that enables payments in multiple currencies worldwide using an Inter ledger Protocol (ILP). In contrast to Bitcoin, Ripple does not replace banks as intermediaries, but provides a platform for the efficient networking of banks’ existing payment systems. The artificial currency “Ripple” (XRP) can optionally act as a bridge currency in order to enable payments to be carried out as quickly as possible, even in illiquid foreign exchange markets. The volume of the XRP artificial currency is limited to 100 billion XRP, which, unlike other cryptocurrencies, is not generated by mining.
- Litecoin: Litecoin, the cryptocurrency launched in 2011, is similar to the Bitcoin system as it is also based on a peer-to-peer network and blockchain methodology. The main difference to Bitcoin is the design of specific blockchain parameters. New blocks are created on the Litecoin network every 2.5 minutes, so the maximum number of Litecoins that can be created is converging to 84 million .
The Bitcoin Industry Ecosystem
An overview of the Bitcoin industry ecosystem, which consists of the developers of the Bitcoin core software and the miners, as well as providers of retail services (wallets), operators of trading platforms (Bitcoin exchanges), payment transaction solutions and other value-added services.
Wallets are software solutions that allow end customers to receive, send and manage bitcoins. There are now a large number of wallet providers. The best-known wallets, which are available for all common operating systems, include the Bitcoin Core Armory, MultiBit, Electrum and Mycelium. Miners are computer networks that systematically validate new transactions in competition and combine them into new blocks. Since the probability of generating new blocks increases with computing power and at the same time the mining revenue decreases over time, the business model of the mining pools is geared towards economies of scale. The largest mining pools include F2Pool, Bitfury, CEX-IO and Ant Pool. Due to the high energy consumption, there are numerous mining pools in China. Other providers position themselves as operators of exchanges for cryptocurrencies, through which one can buy and sell cryptocurrencies among themselves or against real currencies. The largest bitcoin exchanges currently include OKCoin, Kraken, Coinbase and Bitfinex. Payment transaction services with extended functionalities are offered, for example, by Circle, bitpay, Coinkite or Gocoin.
Market development and prospects
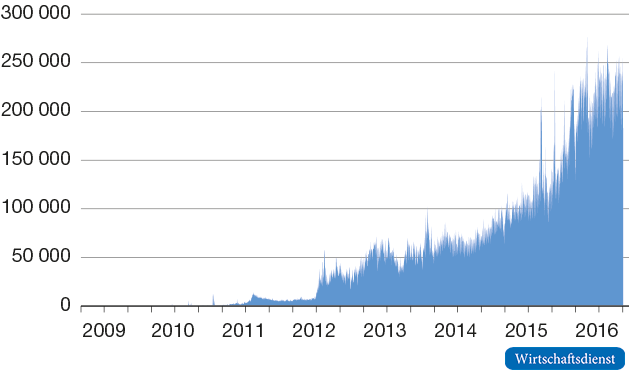
Although the number of providers in the Bitcoin industry has multiplied in recent years, there can be no talk of a breakthrough in user acceptance. Figure 4 shows that although the average number of Bitcoin transactions per day has grown significantly, it is currently only around 250,000 worldwide. Compared to credit card systems such as Visa or Mastercard, the importance of bitcoins is still marginal . In 2014, for example, the number of transactions from Visa was almost 100 billion. Overall, the growth momentum and the rate of diffusion of bitcoin seem too low to pose a threat to established payment systems in the foreseeable future.
A key reason is likely to be an aspect that the protagonists of Bitcoins repeatedly mention as an advantage of this artificial currency: the lack of a central authority such as a central bank, which ultimately ensures credibility in the currency’s stable value through a monetary policy geared to price stability target. The anonymity of virtual currencies in particular is apparently a key barrier to broader acceptance, since potential causes of financial damage, for example as a result of the theft of private keys during hacker attacks in an anonymous network, can hardly be identified and prosecuted. This has also meant that the Bitcoin network has proven to be particularly suitable for illegal trades in some cases. The most famous case is the “Silk Road” platform, which gained notoriety as ebay for illegal transactions and was shut down in October 2013. Added to this was the bankruptcy of the bitcoin exchange Mt. Gox in 2014 and the loss of an estimated US$ 70 million by the Hong Kong-based bitcoin exchange Bitfinex as a result of a hacker attack, which was only reported in August 2016.
Another aspect is the low market entry barriers for establishing such artificial currencies. Basically, all you need is a cryptographic method for encryption, a mining process and a consensus algorithm, which are coded in open source software and made publicly available. The high number of artificial currencies underlines that in most cases this is not likely to be a viable business model.
The high level of uncertainty about the future of bitcoins is also manifested in the volatile price development. The trading volumes on the various bitcoin exchanges are manageable and investments in virtual currencies can be classified as highly speculative. Figure 6 shows that Bitcoin’s value has peaked at more than $1000 while it currently fluctuates between around $600 and $700.
Disruption through distributed ledgers
The actual potential for disruption does not come from the virtual currencies themselves, but from the blockchain technology used. It should be noted that the blockchain is just one variant of distributed ledger technology. Basically, distributed ledgers are distributed account management systems in which digital data is shared, replicated and synchronized across multiple locations. A forgery-proof mapping of transactions is made possible with the help of cryptographic methods. If the transactions are mapped in interconnected blocks using a proof-of-work method, this is referred to as a blockchain.
There are various design options for distributed ledgers, which differ in terms of the number of users, the cryptographic methods used and the procedures used to check the integrity and correctness of the database at all times. The cryptocurrencies are based on so-called public distributed ledgers, which are basically open to any user who has the necessary software. New transactions that lead to a change in the database are combined into new blocks based on a consensus algorithm and can be validated by each network node. Since the anonymity associated with open distributed ledgers such as Bitcoin must be viewed critically, especially from the point of view of money laundering,
These distributed ledgers, also known as “private” or “permissioned”, are operated by a defined number of members. The use of encryption techniques is intended to ensure that transactions in a closed multilateral settlement system are processed in real time, as far as possible. In addition, increases in efficiency are to be made possible through the joint use of databases (shared ledger). Participation usually takes place via a proof-of-identity procedure in which each participant has to undergo a registration process. This makes it possible to draw conclusions about the identity of the respective user in the event of fraud. However, in individual cases it might be a challenge to structure the access rights in such a way that that transparency and verifiability of the database entries on the one hand and the right to data protection on the other can be reconciled. In the case of private distributed ledgers, the ongoing validation of the transaction directory can also be carried out by network nodes classified as trustworthy or the operators of the database.
The development of distributed ledger technology is still in the early stages, so that the potential of the technology can currently only be grasped in rudimentary form. However, it is to be expected that transaction and information-intensive industries in particular will be exposed to disruptive changes through the use of distributed ledgers. This includes the financial sector and above all “transaction banking”. This includes all services provided by banks in connection with the processing of payment transactions and foreign exchange and securities transactions.
payment transactions
The processing of payment transactions in the euro zone has made significant progress with SEPA (Single Euro Payments Area) and the Target2 system. Because with SEPA, the single euro payment transaction area, uniform procedures for cashless payment transactions were introduced throughout Europe. The Target2 system is the payment system of the central banks of the Eurosystem for the fast processing of transfers in real time. Nevertheless, transfers by end customers, even within the euro zone, are usually only valued on the next bank working day. These settlement periods can be significantly longer when it comes to international transfers via the SWIFT system, where the settlement of payments is processed via correspondent banks.
Payment transactions in particular are predestined for the use of distributed ledger technology. Similar to the bitcoin network, cross-border payments in non-anonymous peer-to-peer networks could also be carried out in real time between the contracting parties in the future, without the need for additional intermediaries. So far, even web-based payment systems such as Paypal still require banks and credit card companies as service providers.
However, such “instant payment systems” do not necessarily have to be based on blockchain technology, but can certainly be based on a further modernization of Target2 or specific transaction-oriented messenger services. In Europe, the European Central Bank and the European Retail Payments Board (ERPB), founded in December 2013, are driving the development of a real-time payment system based on SEPA formats and the development of the associated regulations.
investment services
Significant increases in efficiency are to be expected for investment services, especially in post-trading activities. Although these activities vary depending on the complexity of the financial products, they basically take place in the following steps: After the purchase or sale orders have been received, the order routing of an intermediary (bank/broker) is used to forward them to an electronic or physical trading platform. Then the clearing takes place. This means the determination of mutual claims and liabilities and delivery obligations. During the subsequent settlement, the security is transferred and, in return, the corresponding amount of money is transferred. Banks and brokers act as intermediaries between the buyers or sellers and the central securities depositories.
For example, the settlement time for stock trading with securities held in collective safe custody is currently two days. Money regulation within the euro zone is usually carried out via the Target2 system. With Target2-Securities (T2S), a central securities settlement in central bank money will be implemented in various stages up to 2017, with securities custody and the associated services remaining with the national central depositories (Central Securities Depositories). The T2S concept is based on bringing together the central bank money and securities side on one platform in “delivery versus payment mode”. Cross-border securities settlements remain much more complicated if at least one transaction partner is based outside the euro zone.
Distributed ledger technology can contribute to a significant streamlining of processes here. If it is possible to transmit security transactions in a distributed database using cryptographic methods in a forgery-proof manner, the current time-consuming clearing and settlement processes can be merged in the final stage of development to such an extent that trading and settlement can take place almost in real time. This could mean that today’s central securities depositories mutate into a pure depository and that the custody services of the banks no longer have to exist in this form. Because dividend or coupon payments can also be automated via smart contracts as an application on the blockchain.
Smart Contracts
Smart contracts represent the digital representation of contractual agreements that are encoded in the distributed ledger as executable programs. These enable activities to be triggered automatically if their execution is linked to the occurrence of certain contractual conditions. This can affect interest and principal payments as well as purchase price discounts, credits or the automatic adjustment of insurance premiums depending on the damage history.
The principles of distributed ledger technology can also be applied outside of the financial sector to material transaction objects such as real estate, machinery and equipment or the transfer of intangible assets such as intellectual property rights. If these assets are recorded electronically via sensors, RFID transponders, a QR code or an IP address, transmission processes can be digitally mapped and tracked in a distributed ledger such as a blockchain.
smart government
This makes virtual notary services conceivable for real estate transactions or the sale of companies with the help of cryptographic processes. Distributed ledgers can also help to streamline the efficiency of administrative processes in the public sector (smart government), for example if all tax-relevant data from private individuals, companies and public institutions can be made available in a distributed database and assigned in real time in a tamper-proof manner. This would make tax evasion much more difficult, and tax returns could be created more easily or, ideally, automatically by intelligent apps. The keeping of land registers and cadastres is just as suitable for a blockchain solution as numerous services of the registry offices.
There are similar starting points in healthcare (smart health), for example by making patient data or treatment processes available to clinics, doctors and insurance companies in a distributed database. For data protection reasons, the granting of access rights would remain with the patient. Administrative processes in medical care could be streamlined and data for research projects could be made available more quickly and comprehensively in an anonymous form.
In conjunction with smart contracts, distributed ledgers can also promote the development of Industry 4.0, which is based on the merging of virtual and physical systems into so-called cyber-physical systems in industrial production. Because in numerous industries it is important to reliably record the origin, authenticity, quality or compliance with environmental standards. This applies, for example, to the food industry when verifying organic forms of cultivation, to the raw materials industry when examining mining rights or to the textile industry when examining working conditions in the producing countries. In all of these cases, it is conceivable to document the production, transport and further processing of products completely and forgery-proof in a distributed ledger. The falsification of indications of origin, non-compliance with quality standards or improper disposal of residues would be made considerably more difficult. The distributed ledger technology can therefore trigger disruptive changes in different areas and thus develop into a key technology within IT. Therefore, increased funding for research in this area should be considered.
Lexicon
– Address: A Bitcoin address is like a physical address or an email address. This is the only information you need to provide for someone to pay you with Bitcoins.
– Block: A block is an addition in the blockchain that contains and confirms several pending transactions. Approximately every 10 minutes, a block is added to the blockchain via mining. A block generally groups between 1000 and 3000 transactions and is completed by a header which, in addition to its checksum, contains among other things the identifier of the previous block. From any block, it is thus possible to go back to the initial block of the chain by checking its validity at each step.
– BTC: BTC is the unofficial ISO code for Bitcoin, the official code being XBT. BTC is often used as an abbreviation, similar to USD for the US dollar.
– Blockchain: Blockchain is a public log of all Bitcoin transactions, in chronological order. This is shared between all users of the Bitcoin network. And it is used to check the balance of Bitcoin addresses and to prevent double spending.
– Private Key: A private key is secret information that proves your right to spend bitcoins from a bitcoin address defined by a cryptographic signature. Each bitcoin address has its own unique private key. Your private keys are stored on your computer if you use a software wallet while they are stored on online servers if you use an online wallet. Private keys should never be revealed because they allow the bitcoins of the Bitcoin addresses with which they are associated to be spent.
– Confirmation: A confirmation means that a transaction has been verified by the network and that its chances of being reversed are almost non-existent. A single confirmation offers a good level of security. Although for large payments (eg $1000 USD and above), you can wait until a transaction has accumulated more confirmations – 6 confirmations is the most common norm. Each new confirmation decreases the risk of a reversal exponentially.
– Cryptography: Cryptography is a branch of mathematics used to create mathematical proofs that offer a high level of security. Nowadays, any online business or bank already uses cryptography. With bitcoin, cryptography is used to prevent anyone from spending another user’s funds and to prevent corruption of the blockchain. It can also be used to encrypt a wallet, so that it can only be used with a password.
– Double Spend: If a malicious user tries to spend his Bitcoins on two recipients at the same time, this is double spend. Both mining and the blockchain exist to create a consensus to decide which of the two transactions will be confirmed.
Hash time-lock contracts (HTLCs): these are contracts that only execute under certain conditions (one of the parties must provide the correct hash satisfying these conditions for the payment to be made). In the case where there are multiple parties, it is possible to use a network of payment channels rather than being limited to two users: this allows users not to have to constantly open channels.
– Payment channel: payment channels allow two parties to carry out transactions without however registering all of them in the blockchain. These two parties do not necessarily trust each other and the opening of a channel therefore requires programming a contract which will automatically credit the parties with their coins in proportion to the last state of the channel having been approved by the two participants in the exchange . . It is therefore necessary to sequester the coins used, thanks to autonomous contracts.
– Mining: Bitcoin mining is the process of using computer hardware to perform mathematical calculations for the Bitcoin network to confirm transactions and increase security. As a reward for their services, Bitcoin miners collect transaction fees for transactions they confirm and newly minted Bitcoins. Mining is a competitive market where revenues are divided according to the number of calculations performed. Not all Bitcoin users mine and it’s not an easy way to make money.
– P2P: Peer to peer refers to a form of system that functions as an organized community. Allowing each individual to interact directly with others. In the case of Bitcoin, the network is built in such a way that each user broadcasts the transactions of other users. And no bank is required as a third party between users.
– Wallet: A Bitcoin wallet refers to the equivalent of a physical wallet on the Bitcoin network. Each wallet can display the balance of the Bitcoin addresses it contains. The same way you can count the money in your wallet. A bitcoin wallet also shares the similarity of allowing you to pay a specific amount to a specific person. Unlike credit cards where you are charged by the merchant.
– Signature: A cryptographic signature is a mathematical mechanism which makes it possible to prove its authenticity. In the case of Bitcoin, a Bitcoin address and its private key are linked by the magic of mathematics. When Bitcoin software signs a transaction with the appropriate private key, the Bitcoin network can verify that the signature matches the Bitcoin address in the transaction. Even so, there is no way to guess what the private key is in order to steal hard-earned bitcoins.
– Hash Rate: The hash rate is the unit of measurement of the computing power of the Bitcoin network. The Bitcoin network has to do intensive mathematical calculations for security reasons. When the network reaches a hash rate of 10 TH/s, it means it can do ten trillion calculations per second.
– Transaction: A transaction is a transfer of value between Bitcoin addresses that is included in the blockchain. Bitcoin wallets store secret information for each Bitcoin address called a private key . Private keys are used to sign each transaction, providing mathematical proof that they came from the correct owners. The signature also helps prevent the transaction from being modified once issued. All transactions are broadcast between users and are confirmed by the network within minutes through a process called mining .
– “Fan out” transaction: transaction generally having one entry and a high number of exits
The vocabulary of the crypto trader
Arbitrage : activity consisting of taking advantage of the price difference that there may be between several “exchanges” to buy on one and sell on the other. Thanks to arbitrage, prices tend to equalize on all markets. When significant discrepancies persist, it is often because the fees applied (to the transaction or to the withdrawal) are not the same.
ATH : All Time High, highest price ever reached.
Bear market : market with a downward trend.
Bull market : market with an upward trend. We also use the adjective “bullish” to qualify this situation.
Chart : Price chart.
Correction : Sudden change in price that returns to its previous price (or comes close to it) after a relatively long period of rise or fall.
Day Trading : Activity consisting in speculating in the short term and buying and selling very frequently. The “day trader” is opposed to the “hodler”, the long-term investor.
Dip (fall): sudden and ephemeral fall in the price which immediately regains its value. This may correspond to a major sale by a single player. Dips can be good opportunities for those who have placed buy orders.
DCA (Dollar cost averaging): Investment strategy for large entrants on illiquid markets consisting of buying in several installments to reduce the impact of volatility in particular.
Exchange (exchange platform) : marketplace dedicated to crypto-currencies: Paymium, Kraken, Coinbase, Poloniex, etc.
FOMO (fear of missing out): fear of missing out on an opportunity when the price starts to rise. This fear can lead to bubbles when it comes to a group phenomenon.
FUD (Fear, Uncertainty and Doubt): Fear, uncertainty and doubt. A technique of disseminating negative, often vague and fear-inspiring information with the aim, sometimes, of lowering the price and/or discrediting a project.
FUDster : one who practices FUD.
FIAT (Fiat money): currency issued by central banks, which is based on the confidence that we have in these issuing institutions. Example: $, €, £…
Hodl : comes from the word “hold”, which means to hold”. The “hodler” invests for the long term.
ICO Initial Coin Offering : Raising funds in cryptocurrency by issuing and selling a token.
Limit buy : Buy trigger order placed by the investor to buy crypto-currencies at a price fixed in advance.
Limit sell : Trigger order to sell at a price fixed in advance.
Long position : bet on the rise using margin trading . That is, borrowing cryptocurrencies hoping for a rise that will both repay the cost of borrowing and earn a profit.
Market Buy : purchase order at the market price.
Market cap : Theoretical value of the money supply of a crypto-currency. To calculate the “market cap”, the number of tokens in circulation is multiplied by the price of one unit.
Market sell : order to sell at the market price.
Margin trading : margin loans allowing lenders to take advantage of their dormant capital without risk of default, you can only borrow in proportion to your assets on the platform. The only risk to be assumed by the lender is the security of the exchange. “The good side of margin lending is that it provides additional liquidity to the market, the bad is that it is easy for investors to lose money.” – Zhao Dong, OTC trader.
Moon (moon): expression used by the most optimistic to designate the direction of prices.
Pumping : technique of artificially promoting a project or a crypto-currency with the aim of inducing others to invest, raise prices and sell advantageously.
Pump & Dump : Market manipulation, usually operated by a major player or group of major players, consisting of buying huge amounts of a cryptocurrency in order to artificially raise prices in the hope of creating a feeling of “FOMO” attracting new buyers. When this objective is reached, the pumper turns into a “dumper”: he sells everything before the others to make the most of the profit.
ROI (Return on Investment): return on investment calculated by dividing the profit made by the amount invested. An ROI of 100% means that you have doubled your initial bet.
Sell wall / buy wall : On exchanges, some players choose to place sell or buy orders. When the sell price meets the buy price, a trade (an exchange) takes place. All of these orders go into what is called an “order book”. A “sell wall” is literally a sell wall: a sell order for a large amount or lots of small orders at the same price. The opposite being a “buy wall”.
Short position : betting low using margin trading. That is, borrowing cryptocurrencies and selling them hoping for a drop that will redeem more than the original amount in order to repay the cost of borrowing and earn a profit.
Stack : Refers to all of an investor’s crypto-currency capital.
Stop Buy : Order executed when the price exceeds a certain limit so as not to stay out of the market when a bullish phase seems to begin.
Stop Loss : Order executed when the price goes below a certain limit in order to exit the market when a bearish phase seems to begin.
TA (Technical Analysis): Technical analysis. Graphical representation of the price that attempts to predict future market movements from the past.
Tokens : tokens specific to different crypto-currencies or different projects. Bitcoins are the tokens of the Bitcoin network and ethers are the tokens of the Ethereum network. As part of ICOs, certain tokens are created and deployed on the Ethereum network. They generally follow a standard, called “ERC20”.
Trading bot : program responsible for buying and selling without human intervention following a strategy defined by the programmer.
Whale : An important player with a large capital and whose orders can have an impact on the price.
What Bitcoin Address Type Should I Use?
There are several types of Bitcoin addresses. How can you distinguish between the different address types and what do they actually mean?
Bitcoin started out with a very rudimentary address type. In order to make transactions smaller and thus cheaper , new address types have been developed that reduce the amount of information that is required to issue a received transaction again. Also, these address types added important new features to Bitcoin.
Important: You can use all of these addresses in the same way as they are all interoperable. When you use a BitBox02, your addresses are all stored in the same account, so you don’t have to worry about different address types.
All bitcoin addresses in a wallet are derived from seed words. This means that you can create any address type with a seed and you don’t need a new seed for each address type.
Legacy addresses (P2PKH)
Legacy addresses are addresses that start with the number 1 .
Example: 15e15hWo6CShMgbAfo8c2Ykj4C6BLq6Not
A legacy address is simply the hash of the public key to your private key. When Bitcoin came out in 2009, it was the only way to create an address. Today it consumes the most space in a transaction and is therefore the most expensive address type.
Nowadays there is no good reason to use this type of address as the new types are better in every way. Most people only use this address type if they have an old wallet that is incompatible with newer address types.
In contrast to legacy addresses, pay-to-script hash addresses are not the hash of the public key, but of a script that contains certain output conditions that are initially hidden from the sender. These issuance conditions can be very simple (public key owner A can spend this bitcoin) or quite complex (public key owner B can spend this bitcoin after X time if he reveals a predetermined secret). With this script, P2SH addresses can even use SegWit and save on transaction fees.
Sending to a P2SH address is about 26% cheaper than using a wallet with legacy addresses.
This address type further reduces the amount of information stored in the transaction, since the signature and script are stored in the witness rather than in the transaction.
With this address type you can save another 16% compared to the P2SH addresses, so the savings add up to over 38% compared to the old addresses . Because of these savings, this is currently the most commonly used standard for addresses.
Since some exchanges and wallets don’t support Bech32 addresses yet, they ask the user to send them a P2SH address instead. That is why most wallets still offer the option to create a P2SH or even a legacy address wallet.
Taproot addresses are not used yet. In November of this year, the Bitcoin network will perform the Taproot soft fork. This will enable many new smart contract features for bitcoin addresses and improve privacy when issuing such transactions.
Regular taproot transactions are slightly larger than native Segwit but smaller than legacy addresses. That’s because they’re tied to public keys, not public key hashes. For complex transactions, e.g. For example, taproot addresses save a lot of space and are therefore cheaper.
How do you recognize a bitcoin address?
You can tell the type of a bitcoin address by looking at the first few letters. If it starts with “1”, it is a legacy address. If it starts with “3”, it’s a P2SH address. If it starts with “bc1q” it’s a native Segwit address and if the first 4 letters are “bc1p” it’s a taproot address.
Where can I get a bitcoin address?
You can create a bitcoin address by clicking “Receive” in your bitcoin wallet. You can create as many different bitcoin addresses as you like. For privacy reasons, it is advisable not to reuse an address.
Do I have to change my bitcoin address?
You don’t have to change your bitcoin address. If you want to send your bitcoin to a different address, you need to make a regular transaction to the new address that you created in your wallet.
Which bitcoin address should I use?
Most bitcoin wallets use bech32 (native segwit) addresses by default, which saves the most transaction costs. If your wallet gives you the choice, you should use native Segwit addresses.
How do bitcoin addresses work?
Bitcoin addresses contain information about who can access the bitcoin sent to that address. For example, if you can prove that you have the private key to a bitcoin address, you’re allowed to send a transaction from that address. If you can’t prove you own an address, you can’t send a valid transaction.
What is a private key? – The private bitcoin and altcoin key
To protect the user when dealing with cryptocurrencies, a private key (private key) is created. It represents an essential security factor when dealing with Bitcoins & Co. and validates the sending and receiving of coins or tokens. The private key is necessary above all to protect against access by unauthorized persons.
Private key definition
“A private key is a form of cryptography that allows a user to access their cryptocurrency. A private key is an integral part of bitcoin and altcoins. Its security structure helps protect a user from theft and unauthorized access.”
Private key is a guide to account balance
A private key turns the public key, which is linked to the user’s address in his customer account, into a private key. This is created using a complicated mathematical algorithm and it is almost impossible to reverse this process. This means there is almost no possibility of using the private key to draw conclusions about the public address and information of the account holder. Anonymity in the field of cryptocurrency is one of the fundamental aspects and clear advantages compared to classic fiat money.
Valid signature is generated by private key
The string of alphanumeric characters is 51 digits (51 characters) and is presented in wallet import format. Only those who have the unique key have access to the account and can use the digital wallet. The wallet software creates a digital signature and processes this transaction with the private key. This signature can only be validly triggered and generated with the private key. It ensures that the transaction cannot be changed after transmission and that it originates from a specific user. With just a minor change, the signature would change as well.
Only with the private key can the user of the digital wallet prove that the crypto money in it actually belongs to him. If the wallet contains a large number of cryptocurrencies , a seed is generated, which, in contrast to the private key, consists of a sequence of 12 or 24 words and not numbers. The seed is only generated once, because it can independently create and process all private keys for a wallet.
Private key and public key are connected to each other
Mathematically, the private key is a random number between 1 and 2258 . The result is a number with 51 digits and 2 to the power of 256 variants. The secret key is generated by a random number generator when setting up the digital wallet. At the same time, the software also creates a public key, the public key . Both keys are linked to each other. While newcomers to the crypto world believe that their wallet is the place where their cryptocurrencies are stored, insiders have long known that only the private key was stored there. He then points to the blockchain where the cryptocurrency resides.
A kind of guide to your own account balance on the blockchain . In the case of private keys that are stored on devices and systems that are connected to the Internet, one speaks of hot wallets. This also includes desktop wallets such as Electrum , mobile wallets such as Breadwallet and web-based wallets such as Coinbase . If the wallet stores the private keys offline, this is referred to as a cold wallet. (cold wallet). A paper wallet is also the best choice. For information on how to do this, see our article: Paper Wallet .
How to manage the continual increase of the blockchain?
The blockchain increases by roughly 1 GB every two months. The more time passes, the more difficult it becomes to download it for new users. Satoshi Nakamoto’s initial document mentions a method to compress the blockchain and reduce it considerably: the Merkle tree which summarizes transactions without invalidating the block fingerprint. Once the last transaction for a coin is buried under enough blocks, past transactions can be deleted to save disk space. This function has not yet been implemented.
Furthermore, it is likely that in the medium term users will no longer have a client backing up the entire blockchain. Only super-nodes managed in a decentralized way on dedicated servers will remain, a bit like exit-nodes under Tor, or bittorrent trackers.
How are blockchain divisions handled?
Extract from an article by Jean-Paul Delahaye, computer scientist and mathematician, professor at the University of Lille 1, published on February 15, 2015 on scilogs.fr : “ When several competing blockchains are present on the bitcoin peer-to-peer network, for example following the success almost at the same time in two distant places of the network of two miners, the miners are instructed (programmed in the software they use) to choose between the different blockchains of which they are informed of the existence .
For everyone to choose the same blockchain (search for a consensus) the instruction is to “choose the longest of the blockchains”. This they all do, with the effect of eliminating blockchains except one, the longest. This reconstitutes a coherent state of the system (a single blockchain) and therefore a list of valid transactions which will be the same for all.
The criterion “choose the longest blockchain” at first meant “choose the blockchain with the largest number of pages”. We realized that it was dangerous because anyone could make a fake blockchain with a larger number of pages than the others by rebuilding everything from the beginning and not making the difficulty of the problems evolve as quickly as for the real blockchain, and therefore by solving only easy problems for each new page. If the criteria “longest blockchain” had meant “chain with the most number of pages”, it would have been easy to seriously disrupt the blockchain, and… bitcoin would probably not exist for a long time.
The length of the chain is now defined by “the chain having the highest cumulative hash rate (we add the average difficulty of each block)”. In other words, what counts is the quantity of calculations actually deposited in the blockchain, and it is the one that contains the most that is considered valid. It is no longer possible to fabricate an entire fake blockchain cheaply. Doing a mock blockchain really requires a cumulative computation at least as large as that enshrined in the real blockchain.
Making a fake blockchain is only possible for someone who alone has a greater ability to calculate hashes than all the others put together. This is the idea of 51% attacks, which are potentially devastating.
The definition of the “length of a blockchain” as used by the bitcoin protocol is therefore a crucial detail. It means without any doubt that the blockchain contains calculation and that it is this content in calculation which distinguishes it from other possible false blockchains that we could try to replace it. The notion of computational content is at the heart of the bitcoin protocol.
How is the “blockchain” constituted?
The “blockchain” is the Bitcoin transaction log. This register is made up of a series of chapters (blocks) which follow one another, each grouping together the transactions carried out in a certain period.
Gérard Dréan explains the formation of this chain of blocks as follows:
“The blockchain is a set of blocks, protected against any modification, each of which contains the identifier of its predecessor […]. It can have the shape of a tree with several branches. The longest of these branches, called the main branch, is identified by the identifier of its terminal block. From this identifier, it is possible to trace this main branch back to the original “ Genesis ” block, created by “ Satoshi Nakamoto ” on January 3, 2009, and thus find all the transactions recorded since.
Each node in the network constantly receives all kinds of messages, some of which offer new blocks to add to the blockchain. A fundamental security principle is to make the assumption that other nodes in the system may be faulty or fraudulent. Each node must therefore consider everything it receives from other nodes as suspect in principle, determine its nature itself and validate it independently before using it.
If a message contains a block, this is submitted to a protocol which may or may not add it to the local blockchain, and the complexity of which stems from the fact that it must deal with all special cases, even those which seem a priori the more unlikely.
In addition to transactions, each block contains a checksum (“hash”) which protects it against modifications, and also serves as an identifier. It also contains the identifier of the block that precedes it in the blockchain of the miner who created it, as well as a measure of the amount of work that went into producing it. The first step therefore consists in eliminating the new block if it is badly formed (incorrect syntax) or if it has already been received, and therefore has already been processed.
A fundamental goal of the blockchain construction protocol is that all of its copies be identical, albeit independently constructed. It therefore aims to obtain a consensus on the same version of the transaction log for all computers on the network. The principle adopted is to choose, among the possible versions of the blockchain, the one whose construction required the greatest amount of work, which aims in particular to deter potential fraudsters by requiring them to work greater than that of the nodes. honest”.
If the new arrival is kept, the continuation depends on the block that it indicates as its predecessor. If this is not indicated, the new block is kept among the “orphan” blocks. If it is indicated but does not exist in the local blockchain, the new block is also placed among the “orphan” blocks, but in addition its predecessor is claimed from neighboring nodes. This step allows for example the reconstitution of the blockchain of a node which has been stopped for a certain time. In both cases, the program goes back to waiting for a new block. Indeed, all the blocks received are treated in the same way regardless of their origin.
If the specified predecessor is the current end of the main branch, the program tries to add the new block to it. To do this, it checks that each transaction in the block is syntactically valid, is not already present in the blockchain and satisfies the validity condition indicated by its “version” code. As soon as a transaction is invalid, the process is aborted. Otherwise, the identifier of the new block replaces the identifier of the end of the blockchain, all transactions of this block are eliminated from the pool of pending transactions and this block is sent to neighboring nodes, which will perform the same process.
If the indicated predecessor is another block than the terminal block of the current blockchain, two cases can arise depending on whether the sequence of blocks that leads to the new block has required more or less work than the current main branch. If it required less work, the current blockchain is not modified, and the new block is simply kept in memory, forming the start of a secondary branch. If this new branch required more work, it should become the reference blockchain. To do this, the program goes back to the fork, and from there, tries to successively add each of the blocks of the new branch that have been put on hold without being validated, checking as above the validity and legitimacy of the transactions it contains.
If it succeeds without encountering a block or illegitimate transaction, it updates the pool of pending transactions (removing the transactions that are now in the new main branch and putting back those that were in the old branch main and are not in the news), it replaces the identifier of the end of the blockchain and broadcasts the block to neighboring nodes. Otherwise, it leaves the blockchain as is, while keeping the new block pending as before.
Finally, if the new block is indicated by one or more orphan blocks like their predecessor, the protocol tries to link the orphan blocks to the blockchain through it by recursively applying the above protocol to it.
The protocol in normal operation
In normal operation, the blockchain is identical on all nodes, and the new block designates the terminal block of the existing blockchain as its predecessor. Each node will therefore add the first valid block it receives to the end of its main branch. However, miners work in parallel and there is no general rule regarding the selection of transactions to be incorporated into a block. From the same pool of raw transactions, miners can therefore offer different blocks, which each node will continue to receive after the one it has added to its copy of the blockchain, which will designate the same predecessor and will partly contain the same transactions. He will therefore keep them without checking them, making them the beginnings of secondary lateral branches.
If all nodes in the network receive blocks from miners in the same order, the blockchain remains the same on all nodes, although each has built its own version of it independently. But it can happen that two or more miners issue different blocks in a time less than the propagation time of the blocks in the network. These blocks then arrive in a different order depending on the receiving nodes, which will each retain the first to arrive in its main branch, the following blocks being grafted as is on the side. The nodes then separate into two populations (or even more) and there is a bifurcation (“fork”) of the blockchain. In particular, miners from each population are now working from different blockchains.
This situation is usually resolved by the following blocks. Indeed, the situation that gave rise to this bifurcation is very unlikely, and it is less and less likely that it will happen again in the next stage. There will come a time when the first block received will be the same for everyone, and the application of the protocol described above will cause it and its predecessors to then become the main branch for everyone. At that time, transactions that were in the old main branch, and were therefore considered final, may no longer be in the new one. This is why it is recommended to consider a transaction as final only if the block in which it appears is at a certain distance from the current block (6 blocks for normal large transactions,
Fraud cases
Normally all the actors in this process have the same objective: to ensure the proper functioning of the system. But anyone can freely issue transactions, become a miner or a node in the system, including with malicious intent or with non-standard versions of software. No participant can therefore rule out the hypothesis that what he receives is erroneous or even downright fraudulent or dangerous, and everyone must verify its validity at all stages. Erroneous or fraudulent transactions or blocks have almost no chance of escaping these checks and reaching the blockchain, and the fraudster very quickly finds himself isolated.
A node can create fraudulent transactions. But the only possible way to introduce them into the multiple copies of the blockchain is to incorporate them into a block and submit this new block to the other nodes of the network through the normal route. Absent equally fraudulent changes to block construction protocols and transaction validation processes, these transactions will not be validated and incorporated into legitimate blocks, nor accepted by other nodes. The blockchains of “honest” nodes will therefore not be affected and the fraud will have no consequences other than local to the fraudulent node.
To modify an existing block in the register, the only way is to create a new block possibly containing part of the transactions of the old one, and to try to graft it in its place. This new block will be grafted (without verification) next to the block it seeks to replace, but the main branch will remain unchanged.
For it to become part of the main branch, new blocks would have to be grafted to it faster than to the real main branch so that this new branch would eventually overtake it. However, during this time, the rest of the network continues to lengthen the main branch. Each of the new blocks having to be recalculated ex nihilo including its checksum, the fraudster(s) would have to mobilize a total validation power greater than that of the rest of the network. In addition, each of these blocks, as well as the validity and legitimacy of the transactions it contains, would be checked against the part of the blockchain located upstream of the bifurcation. It is difficult to see which fraudulent modifications could escape these checks,
In the end, even if a fraudster managed to introduce modifications of this type in certain nodes, he would thus create a small group of users isolated from the rest of the network and who could only exchange with each other, which is difficult to see. interest. The rest of the network would not be affected. In addition, the maneuver would necessarily be visible, especially since the replaced block is older, since it would consist of the abnormally rapid creation of blocks coming to be grafted upstream of the current end. The fraudster would have every chance of being eliminated, and the affected blockchains would be repaired from those that remained intact.
How does the network reach consensus on chain of transaction?
To be able to validate the transactions, they must all be public. Then they are put one after the other in a single long chain. As long as the whole network agrees on which channel is the right one, it is impossible to have two transactions from the same person with the same bitcoin.
To agree on which channel is the correct one, since there can be two transactions made at the same time, but whose publication happens in a different order depending on the distance between the transmitters and the receivers, the channel kept is the longest.
It may be that for some time several chains are side by side, but eventually, one will be completed more quickly than the other and the transaction will then be confirmed.
What is a hash function?
Hash functions – in particular SHA-256 for Bitcoin – are mathematical functions which make it possible to transform a string of characters of any length into another string of fixed length (256 bits, or 64 characters in full hexadecimal notation for SHA -256 ). Characteristic: the most insignificant change in the input string causes a large change in the output string
Merkle Trees — An Introduction to Concepts and Components
The problem:
In a centralized network, the data is usually accessed from a single source, so not much work is required to organize a single copy of the data and nobody has any choice but to trust the system.
However, in a decentralized network with multiple nodes, it is important to organize the data efficiently. In a blockchain where the data is distributed, the challenge is firstly to access the data efficiently and secondly to verify it while correctly distributing a copy of the data to all nodes.
The solution:
Implementation of Merkle trees in systems based on decentralized networks to share and verify data.
Merkle trees reduce costs by:
- Organization of the data so that no computing power is required for sharing and reviewing it.
- Efficient execution.
The Merkle Tree concept
A commonality among the implementations of Bitcoin, Ethereum, IPFS, Git, Apache Cassandra, and BitTorrent is the technique for storing data known as the Merkle tree , a fundamental component of a blockchain that allows for efficient and secure verification of large data structures.
Merkle trees are used to store and organize all transactions in a block of a blockchain and to check the consistency of the data.
A Merkle tree is a binary hash tree where the value of an inner node is the hash value of its leaf nodes. The hash values of the transactions are located at the root of the Merkle tree and are referred to as leaf or child nodes.
Each leaf/child node of the Merkle tree contains the hash of the transactions, followed by the intermediate nodes, which contain the hash of the leaf/child nodes’ “combined hash values”, and then follows the root node, which contains the combined hash values of its left and right trees, known as the Merkle Root.
Interestingly, when we want to make changes in a particular transaction, the hash value of the intermediate node changes, which leads to a change in the root hash value at the same time. That is, if someone tries to modify a specific transaction, the root hash will be modified, and once the root hash changes, all subsequent hashes of all existing blocks will be modified since they are connected. In this way, no attacker can try to manipulate the data, because to do so he would have to change the transaction data of the entire chain, which is of course an impossible task. That’s the beauty of designing a Merkle tree, which makes it a tamper-proof data structure.
Merkle trees ensure the integrity of the data, so you don’t have to go through the entire transaction to see its verifiability. The tree can be broken down into small chunks of data that can be used to verify transactions across the network. This concept is known as Merkle Proofs and is of great advantage in decentralized systems. Rather than having to verify all information in the entire tree, Merkle Proofs only require enough computing power to verify a small amount of data for accuracy.
applications
- Merkle trees are used to synchronize data in decentralized and distributed systems where the same data should exist in multiple places.
- They are also used to check for inconsistencies in the data and detect inconsistencies between replicas of the entire database.
Major Benefits
- Merkle trees improve massive scalability by splitting the data into different parts, as Merkle trees can be broken down into tiny chunks of information for verification.
- This effectively verifies the integrity of the data.
- Any amount of data can be stored in a Merkle tree, always ending in a root hash at the top.
- It offers high-level data and consistency checking.
- Merkle trees significantly reduce costs with the help of Merkle proofs.
How Merkle Trees benefit the Umbrella Network
Because Merkle trees help organize data efficiently so that the verification process requires less processing power, Umbrella Network uses them to bring thousands of real-world data points onto the chain at low cost, without compromising security and data integrity .
In Umbrella Network’s system, each leaf of the Merkle tree represents a data point from an oracle. The Merkle Root Hash is a unique identifier for the entire block of transactions within the Merkle tree. A “Proof of Stake” consensus is performed on the Merkle Root Hash representing all the data in the tree, and the final validated set of transactions is written to the chain for a transaction fee.
Umbrella uses Merkle trees to bundle transactions to solve the scalability problems of today’s oracles. Merkle trees are used to aggregate the data so that multiple transactions can be bundled into a single transaction for a single fee. This significantly reduces the time and cost required to bring real-world data onto the chain, making Umbrella Network the most cost-effective oracle solution with the largest dataset available on the market.
How does Bitcoin’s scripting language work?
“Any transaction is made up of inputs and outputs . Except in the case of generating new bitcoins, each input is the output of another transaction. In Bitcoin, therefore, attention is paid to transactional outputs, and in particular to unspent transactional outputs , almost always referred to as UTXO , short for Unspent Transaction Output.
UTXOs represent the de facto bitcoins in circulation: a bitcoin only exists because it is the result of a transaction and is not included in any other transaction . Even newly minted bitcoins result from a transaction, called a “ coinbase ,” that the miner builds to reward themselves.
During a Bitcoin transaction, input UTXOs are unlocked and new UTXOs are locked . Of course, the outgoing amount cannot exceed the incoming amount. The locking and unlocking of UTXOs is done through scripts whose execution is done during validation by the nodes of the network. The transaction is only carried out when the scripts are valid in the eyes of the network: if one of them is invalid, the transaction is rejected.
In the case of a transaction between simple addresses, the unlocking scripts consist of verifying the signatures which correspond to the input addresses. Lock scripts, on the other hand, consist of locking funds at outgoing addresses.
Bitcoin’s scripting language works with a stack , like some 60s languages like Forth . Please note: we are not talking here about an electric battery, but about a data battery! The data is placed on the stack and operation codes (opcodes) act on this data. The language is rich: there are more than a hundred opcodes, as evidenced by the Script wiki page .
What is a SVP wallet?
SPV (Simplified Payment Verification) wallets are the most used Bitcoin clients.
They allow you to send and receive bitcoins without having to have a complete copy of the blockchain on your hard drive or on your phone. To do this, they simply download the headers of the blocks and the transactions concerned.
They therefore do not have the same level of security as a full node and above all do not contribute to the security of the network.



Leave a Reply